Soc 1 & 2: Choosing The Right Compliance Report

The biggest hang-up I see with SOC 1 and SOC 2 is people trying to figure out which one they need. The answer is surprisingly simple: it all comes down to what your customers are worried about.
Is their auditor breathing down their neck about financial reporting? Or is their CISO asking how you protect their data from a breach?
Defining SOC 1 and SOC 2 Reports
At the end of the day, choosing between SOC 1 and SOC 2 is about understanding the primary risk you help your customers manage. One is about financial accuracy, the other is about operational and data security. Nail this distinction, and you’re on the right path.

Financial Integrity vs. Operational Trust
A SOC 1 report is built for a very specific audience: your client’s financial auditors. It focuses on your internal controls that could impact their financial statements—what the AICPA calls Internal Control over Financial Reporting (ICFR).
Think about services like payroll processing, revenue recognition software, or claims administration. If your system messes up, it could cause a material misstatement on your client’s balance sheet. That’s why their auditors need your SOC 1 report to complete their own financial audit.
A SOC 2 report, on the other hand, is all about trust and security. It’s designed to give customers confidence that you’re responsibly managing their data. The report is based on the AICPA’s five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
The audience here is much broader—it includes current customers, enterprise prospects, business partners, and regulators. They aren’t worried about their financial statements; they’re worried about you causing a data breach, having an outage, or mishandling sensitive information. Digging into a SOC 2 report example is the best way to see how these controls are actually tested and presented.
Here’s the acid test: If your service going down could cause a financial reporting error for your customer, you need a SOC 1. If your service going down or getting breached would cause a data loss or operational headache, you need a SOC 2.
Quick Comparison: SOC 1 vs SOC 2
To put it all in one place, here’s a high-level breakdown of the key differences.
| Attribute | SOC 1 | SOC 2 |
|---|---|---|
| Primary Purpose | Report on controls relevant to a client’s internal control over financial reporting (ICFR). | Report on controls related to the security, availability, and confidentiality of a system. |
| Core Focus | Financial Controls & Reporting | Security & Operational Controls |
| Typical Audience | Your clients’ management and their external financial auditors. | Customers, prospects, business partners, and regulators. |
| Governing Standard | SSAE 18, specifically AT-C section 320. | AT-C sections 105 and 205, based on the Trust Services Criteria. |
This table gives you the basics, but the real decision depends on who’s asking for the report and why. One report satisfies financial auditors, while the other satisfies security-conscious customers.
To get right to the point, the SOC 1 vs. SOC 2 debate comes down to one simple question: who is asking for the report, and why?
Your answer to that question reveals everything. It’s not about which report you think is better; it’s about meeting the specific demands of the people who keep your business running—your customers and their auditors.
SOC 1: All About Financial Integrity
A SOC 1 report is laser-focused on one thing: making sure your service doesn’t mess up your clients’ financial statements. The audience is tiny and specialized, usually just your client’s management team and, more importantly, their external financial auditors.
These people don’t really care about your broader security posture. They have a single, critical job: to sign off on their client’s financial statements. They need proof that your service—and the controls you have around it—won’t introduce errors that could lead to a material misstatement. Think of it as a crucial piece of financial due diligence.
Let’s say you run a SaaS platform that handles subscription billing and revenue recognition. Your service is literally calculating numbers that will end up on your clients’ income statements.
Their financial auditor is going to come knocking with questions like:
- How do you know your revenue calculations are accurate?
- What stops an unauthorized employee from changing a customer’s billing plan?
- How do you prevent someone from creating fake transactions?
Your SOC 1 report is the answer. It gives the auditor the evidence they need to trust the data coming out of your system without having to spend weeks testing it themselves. It’s a “trust us, we’ve got this handled” document for the financial world.
The core driver for a SOC 1 report is validating Internal Control over Financial Reporting (ICFR). It’s basically a sub-report that your client’s auditor uses to complete their own, much larger financial audit. If your service touches a client’s money or financial data flows, this is for you.
SOC 2: Built on Operational Trust
A SOC 2 report, on the other hand, is all about proving you can be trusted with your customers’ data. The audience here is much, much broader: think prospects, current customers, business partners, and even regulators. Their concern isn’t financial accuracy; it’s operational and security reliability.
The demand for this kind of proof has exploded. SOC 2 is now table stakes for any serious B2B SaaS company because it’s the standard for demonstrating you manage data responsibly. A SOC 2 audit evaluates your controls against up to five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. The market growth is particularly strong for SOC 2 Type II reports, which prove your controls are actually working over time—not just designed well on paper. You can find more details on these trends in the SOC reporting services market analysis.
Imagine you’re a cloud storage provider where enterprise clients store sensitive R&D documents. A potential customer’s CISO isn’t going to ask about your billing controls. They’re going to hit you with a completely different set of questions:
- How do you encrypt our data, both at rest and in transit?
- What are your uptime guarantees and what happens if you have an outage?
- Who can access our confidential files and how do you log that activity?
A SOC 2 report answers these questions head-on. It’s a powerful sales tool that moves you past the security review faster and builds the foundation of trust needed to close enterprise deals.
The choice between a SOC 1 & 2 audit boils down to this: are your key stakeholders wearing green eyeshades or CISO hats?
Comparing Report Scope and Control Environments
The real difference between a SOC 1 and SOC 2 report comes down to what the auditor is actually looking at. While both reports examine internal controls, their focus couldn’t be more different because they’re designed to address entirely separate risks. Think of it this way: a SOC 1 audit is a sniper rifle, and a SOC 2 is a wide-angle lens.
A SOC 1 audit is laser-focused on financial risks. Its scope is strictly defined by control objectives that directly impact a client’s Internal Control over Financial Reporting (ICFR).
In contrast, a SOC 2 audit takes a much broader, operational view. Its scope is shaped by the Trust Services Criteria (TSC), a set of principles covering the security, availability, and integrity of the systems a service organization uses to handle customer data.
Defining the SOC 1 Scope
In a SOC 1 audit, every control tested must tie back to a potential impact on a user entity’s financial statements. You and your auditor will collaborate to define specific control objectives that are relevant to the services you provide. There’s no generic checklist here; it’s all about the money.
Common control objectives in a SOC 1 might include things like:
- Logical Access: Ensuring only authorized personnel can get into systems that process financial transactions.
- Change Management: Making sure changes to an application that calculates client revenue are properly tested and approved to prevent expensive errors.
- Data Processing: Verifying that controls are in place to ensure data processed for clients is complete and accurate enough to support their financial closing periods.
Each objective is directly linked to a specific financial risk. The audit then tests the controls you’ve designed to meet those precise objectives.
Understanding the SOC 2 Scope with Trust Services Criteria
A SOC 2 report is built on the five Trust Services Criteria established by the AICPA. The Security criterion is the mandatory foundation for any SOC 2 audit and is often referred to as the “common criteria.” It’s non-negotiable.
From there, you can add any combination of the other four criteria based on your business needs and the promises you’ve made to customers:
- Availability: Is the system up and running when you promised it would be?
- Processing Integrity: Does the system process data completely, accurately, and on time?
- Confidentiality: How do you protect information that’s been designated as confidential?
- Privacy: How do you handle the collection, use, retention, and disposal of personal information?
The core difference is intent. SOC 1 asks, “Does this control prevent a financial error?” SOC 2 asks, “Does this control protect customer data and ensure system reliability?” The same control can serve both purposes, but it’s tested and evaluated through a completely different lens.
This flowchart neatly shows how the purpose of the report—whether it’s triggered by a financial audit or a customer’s need for trust—steers you down one path or the other.
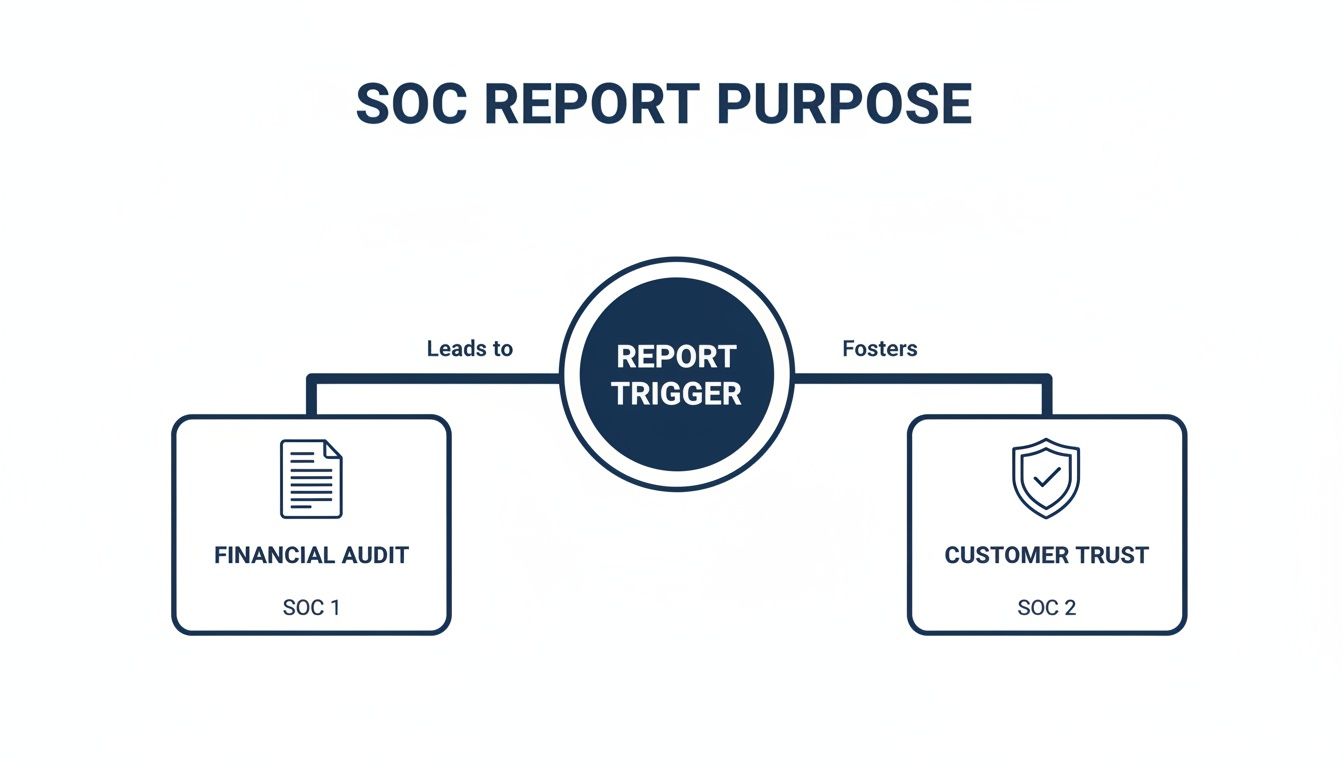
As you can see, a SOC 1 is a direct response to a financial audit need. A SOC 2, on the other hand, is all about proving to customers that you can be trusted with their data.
How a Single Control Is Tested Differently
Let’s take a common control—user access reviews—to see just how much the audit perspective changes. Nearly every company performs these, but how they’re evaluated is entirely different for SOC 1 vs. SOC 2.
In a SOC 1 Audit: The auditor’s main concern is preventing unauthorized access that could lead to a financial screw-up. They’ll ask pointed questions like:
- Are access rights to the billing system reviewed every quarter?
- Is there documented approval from a department head for anyone who can modify customer invoices?
- Are terminated employees removed from the financial reporting software within 24 hours?
The focus is incredibly narrow: protect the systems that touch the financial data.
In a SOC 2 Audit: The auditor’s lens widens considerably to focus on overall data protection and security. They’ll ask broader questions, such as:
- Are access rights to the production environment storing all customer data reviewed regularly?
- Are you applying the principle of least privilege, ensuring engineers only have the access they absolutely need to do their jobs?
- Is access to sensitive data logged and monitored for suspicious activity?
Here, the focus is expansive: protect all sensitive customer data and the systems it lives on. Getting your head around this is a key part of understanding the difference between SOC 1 and SOC 2 reports. While the control itself is the same (reviewing user access), the risk it’s meant to address and the evidence needed to prove it works are worlds apart.
Navigating Type 1 vs. Type 2 Reports
Once you’ve settled the SOC 1 vs. SOC 2 question, there’s another critical choice to make. Both reports come in two flavors: Type 1 and Type 2. This decision is huge—it signals the maturity of your security program and the level of assurance you can offer customers.
Getting this right is key to aligning your audit with your actual business goals.

Type 1: The Blueprint
A Type 1 report is a snapshot. It assesses your controls at a single point in time, like a photograph taken on a specific day. The auditor’s job is to look at the design of your controls and confirm they’re suitable to meet the required objectives.
Think of it as an architectural blueprint. It answers the question, “Do you have the right controls designed on paper?” This is a perfectly fine starting point, especially for startups dipping their toes into the SOC world for the first time.
Type 2: The Surveillance Footage
A Type 2 report goes much, much deeper. It doesn’t just look at the design; it tests the operating effectiveness of your controls over a period of time, usually between six and twelve months.
If Type 1 is the blueprint, Type 2 is the security camera footage that proves you followed that blueprint every single day. It answers a far more powerful question: “Did your controls actually work as intended over the long haul?”
This is the report that sophisticated enterprise customers demand. It provides a much higher level of assurance. For a more detailed breakdown of what this means for evidence collection, check out our guide on the SOC 2 Type 1 vs Type 2 differences.
A Type 1 report shows you have a plan. A Type 2 report proves your plan works in practice. This distinction is the core of building long-term trust with stakeholders, whether they are focused on SOC 1 & 2 requirements.
Strategic Use Cases for Each Report Type
Choosing between a Type 1 and a Type 2 isn’t just a compliance checkbox; it’s a strategic business decision tied to your company’s maturity and market position.
When a Type 1 Report Makes Sense:
- Urgent Customer Demands: A startup might use a Type 1 to unblock an early enterprise deal quickly, satisfying an immediate need without the long wait of a Type 2 observation period.
- Establishing a Baseline: It serves as a fantastic readiness assessment. You formalize your controls and processes before committing to the marathon of a Type 2 audit.
- Budget or Time Constraints: Let’s be real—a Type 1 is faster and cheaper. It’s an accessible on-ramp to SOC reporting.
When You Absolutely Need a Type 2 Report:
- Winning Enterprise Deals: Mature organizations and anyone serious about selling to large companies will find that a Type 2 report is non-negotiable. It’s the gold standard.
- Meeting Contractual Obligations: Many enterprise contracts will explicitly require a clean Type 2 attestation. No report, no deal.
- Demonstrating Program Maturity: A successful Type 2 audit screams that your security program is stable, consistent, and reliable over time—not just a one-day show.
Ultimately, most companies follow a natural progression. They start with a Type 1 to get their house in order and then graduate to a Type 2 in the following years to prove their controls have staying power. It’s a smart, phased approach to building a rock-solid compliance posture.
Separate vs. Combined Audits: Getting Smart About Scope
For a lot of companies, the choice isn’t just SOC 1 or SOC 2. It’s often both. This is especially true for service providers in fintech, health tech, and any B2B SaaS platform that touches a client’s financial data. When you have different stakeholders with different demands, the real question becomes: Do we tackle these audits one by one, or do we get strategic with a combined engagement?
Think about a subscription management platform. On one hand, it processes financial transactions for its customers, which directly impacts their revenue recognition. That means their clients’ financial auditors will demand a SOC 1 report. But that same platform also handles sensitive PII and mission-critical operational data, so its enterprise customers will want a SOC 2 to prove the platform is secure and available.
This is the classic scenario where a combined audit just makes sense.
The Case for a Combined SOC 1 and SOC 2 Audit
Running two completely separate audits can be a massive drain on your time, budget, and people. A combined audit, on the other hand, is a smarter approach that identifies controls satisfying both reports and tests them simultaneously. The benefits go way beyond just checking a box.
Here’s why it’s a better path:
- Serious Cost Savings: A combined audit almost always costs less than two separate ones. Why? Because auditors test the overlapping controls once, not twice.
- Less Audit Fatigue: Your team gets hit with fewer interviews, evidence requests, and interruptions. This lets them stay focused on their actual jobs.
- A Unified Control Environment: This approach forces you to look at your controls holistically, ensuring financial reporting integrity and operational security are managed as one cohesive program, not in separate silos.
How Auditors Find the Overlap
The magic of a combined audit lies in identifying control overlaps. Many of the foundational controls you build for SOC 2—often called the “common criteria”—are the exact same controls needed for a solid SOC 1. They’re the building blocks of any good governance program.
By testing a control like change management just once, an auditor can satisfy both the SOC 1 objective of preventing unauthorized financial changes and the SOC 2 criterion for maintaining system security. This is the core efficiency driver of a combined engagement.
Here are a few common areas where controls overlap:
- Change Management: Your process for testing and deploying code changes.
- Logical Access Controls: How you grant and revoke user access to systems.
- Risk Management: The formal program you use to identify and mitigate risks.
- Incident Response: Your playbook for detecting and reacting to security incidents.
In a combined audit, your auditor gathers evidence for these controls a single time and maps it to the relevant requirements in both reports. It’s a streamlined process that saves time, money, and sanity. The demand for these reports is only growing; the global SOC as a Service (SOCaaS) market is expected to jump from USD 7.45 billion in 2024 to USD 8.44 billion in 2025. This shows how essential these audits are, particularly in the BFSI sector, where strong SOC 2 compliance can slash data breach costs by 25%. You can get more details on the SOC as a Service market growth on Fortunebusinessinsights.com.
At the end of the day, a combined audit isn’t just a cost-cutting move. It signals a mature understanding of your company’s risk landscape. It proves to both financial auditors and security-focused customers that your control environment is robust, consistent, and managed as a single, unified program.
How to Choose the Right Report for Your Business
Choosing between SOC 1 and SOC 2 feels like a high-stakes decision because it is. Pick the wrong one, and you’ll waste time, burn your budget, and still fail to meet customer expectations. The right choice, on the other hand, can be a game-changer, shortening sales cycles and building immediate trust with prospects.
Fortunately, making the right call comes down to answering a few direct questions about your business and what your customers actually need from you. This simple framework cuts through the noise and helps you focus on the why behind the request so you can confidently decide whether you need a SOC 1, a SOC 2, or both.
The Core Decision Checklist
Work through these questions. Your answers will point you directly to the report that fits your business model and meets stakeholder demands.
1. Do your services directly impact your clients’ financial reporting?
This is the big one. If your platform processes transactions, manages billing, or handles any data that ultimately feeds into your clients’ financial statements—think revenue, payroll, or accounts receivable—the answer is a clear yes. Their financial auditors will absolutely need assurance that your internal controls won’t mess up their numbers.
- Implication: A “yes” here strongly points to needing a SOC 1 report.
2. Do customers and prospects ask for proof of your security, privacy, or availability?
Is your sales team constantly bogged down with security questionnaires? Do enterprise clients demand hard evidence that you can protect their data before they’ll even consider signing a contract? This is about operational trust, not financial accuracy. They want to know you can prevent breaches, keep their data confidential, and maintain service levels.
- Implication: A “yes” to this question means you need a SOC 2 report.
This trend is accelerating, especially in hardware and embedded systems. In the System on a Chip (SoC) market, a staggering 75% of North American firms now hold a SOC 2, a huge jump from just 55% in 2023. As breaches become more costly, major players like AWS now mandate SOC 2 for key partners, proving how security compliance directly enables business growth. You can dig into more insights on the role of compliance in the SoC ecosystem from MarketsandMarkets.
3. Are you being asked for both financial and security assurance?
This is pretty common for FinTech, HealthTech, and any SaaS company managing sensitive data that also has a financial angle. In these cases, one set of stakeholders (your client’s financial auditors) needs the SOC 1, while another group (their CISOs and procurement teams) demands the SOC 2.
- Implication: You’re a prime candidate for a combined SOC 1 & 2 audit. This approach saves a ton of time and money by knocking out both at once.
Your choice isn’t about which report is “better.” It’s about providing the specific type of assurance your key stakeholders require. One satisfies financial due diligence, while the other satisfies operational and security due diligence.
By putting these answers together, you’ll have a clear path forward. The goal is simple: select the report that removes friction from your sales process and meets the explicit compliance demands of your most important customers.
Your SOC 1 vs. SOC 2 Questions, Answered
When you’re navigating the world of SOC reports for the first time, a lot of practical questions pop up. You’re probably thinking about budgets, timelines, and how all these frameworks fit together. Let’s tackle some of the most common questions we hear from founders and business leaders.
What’s the Real Cost and Timeline for an Audit?
Let’s be blunt: there’s no fixed price. Costs swing based on your company’s size, the complexity of your systems, and which audit firm you hire.
For a startup or mid-market company doing its first SOC 2 Type 1, you can expect to invest somewhere between $15,000 and $30,000. If you need the more rigorous Type 2 report, the annual cost typically lands between $25,000 and $70,000, sometimes more if your environment is particularly complex.
Timelines are just as variable. A Type 1 report is a snapshot in time, so the whole process—from readiness to final report—can often be wrapped up in 2-4 months. A Type 2 is a different beast; it requires an observation period to prove your controls are working over time, usually for 6-12 months. That means the entire journey can easily take over a year from start to finish.
Customers Are Asking for Both SOC 1 and SOC 2. Do We Need Both Now?
Not necessarily, and it’s smart to prioritize. If your sales team is getting slammed with security questionnaires from enterprise prospects, start with SOC 2. If your customers’ financial auditors are the ones making noise, focus on SOC 1 first. You don’t have to boil the ocean on day one.
That said, if you’re consistently getting requests for both, a combined audit is your most efficient path forward. It’s a single, coordinated effort where overlapping controls are tested just once, saving you a significant amount of time, money, and internal headache.
The key is to prioritize based on your most urgent business driver. Address the immediate need first, then evaluate whether a combined audit makes sense for the following year to streamline compliance efforts.
How Does SOC 2 Relate to ISO 27001?
This is a classic question, especially for companies with global ambitions. While SOC 2 and ISO 27001 have a ton of overlap in their security controls, they serve different purposes and audiences.
- SOC 2 is an attestation report based on the AICPA’s Trust Services Criteria. Think of it as the go-to for demonstrating security to customers in North America.
- ISO 27001 is the global standard for an Information Security Management System (ISMS). It results in a certification that’s the gold standard everywhere else, especially in Europe and Asia.
The good news is that work done for one framework directly supports the other. For example, the risk assessment you build for your ISO 27001 certification will go a long way toward satisfying the risk management criteria in your SOC 2. It’s common for companies to get both to open up different markets.
Finding the right auditor is the most critical step in your compliance journey. At SOC2Auditors, we replace the guesswork with data. Get transparent pricing, timelines, and verified client feedback to choose an audit firm that fits your budget and goals. Find your perfect SOC auditor match today.