SOC 2 Type 2 vs Type 1 The Definitive Guide for Startups

The core difference between a SOC 2 Type 1 and a Type 2 report comes down to time and depth. Think of it this way: a Type 1 report is a snapshot, capturing your security controls on a single day. In contrast, a Type 2 report is more like a video, showing how those controls actually performed over a period of 3-12 months.
Your choice really hinges on a simple question: Do you just need to prove your security system is well-designed right now, or do you need to demonstrate that it works consistently day in and day out?
A High-Level Overview of Each Report
When a customer asks for your SOC 2 report, what they’re really asking is, “Can I trust you with my data?” Both Type 1 and Type 2 reports answer this question, but they tell very different stories.
A Type 1 report is like an architect’s blueprint; it shows that your security system is designed correctly on paper. A Type 2 report is like a structural engineer’s assessment after watching the building withstand a year of storms, proving it holds up under real-world pressure.
This distinction matters. A Type 1 can be a quick way to check a box and satisfy an immediate sales request, but a Type 2 provides the credible, long-term assurance that serious enterprise buyers demand. Getting this right is the first step in aligning your compliance efforts with your actual business goals.
Type 1 The Point-in-Time Snapshot
A SOC 2 Type 1 audit looks at the design of your security controls at a single point in time. An auditor reviews your policies, procedures, and system configurations to confirm you have the right controls in place to meet the Trust Services Criteria you’ve selected.
It essentially answers the question: “As of today, are your security controls designed properly?” This makes it a popular first step for startups that need to unblock deals quickly without the long observation period a Type 2 requires.
Type 2 The Operational Effectiveness Video
A SOC 2 Type 2 audit evaluates the operational effectiveness of those same controls over a sustained period, usually between three and twelve months. The auditor doesn’t just look at the design; they test if your controls are actually working as intended. This involves sampling evidence, interviewing your team, and verifying that policies are consistently followed.
The Type 2 report is the gold standard in vendor due diligence. It offers historical proof of your security performance, not just a promise. It answers the far more important question: “Did your security controls actually work over the last year?”
For a deeper dive into the foundational elements that underpin trust and assurance, it’s helpful to understand the broader security landscape.

To make this crystal clear, here’s a quick summary of the key differences you need to know when making your decision.
At-a-Glance Comparison SOC 2 Type 1 vs Type 2
This table breaks down the fundamental differences between the two reports across the factors that matter most for your business.
| Attribute | SOC 2 Type 1 | SOC 2 Type 2 |
|---|---|---|
| Audit Focus | Assesses the design of controls at a single point in time. | Evaluates the operational effectiveness of controls over a period (3-12 months). |
| Level of Assurance | Moderate. Confirms your controls are suitably designed. | High. Confirms controls are designed and operating effectively over time. |
| Typical Timeline | Faster (4-8 weeks) | Longer (8-18 months, including the observation period) |
| Customer Perception | Good starting point. Often sufficient for early-stage deals. | Gold standard. Usually required by enterprise and regulated clients. |
Ultimately, while both reports serve a purpose, the market has clearly shown its preference. A Type 1 might get you in the door, but a Type 2 is what closes the deal with mature, security-conscious customers.
The Critical Difference in Audit Scope and Evidence
It’s easy to get lost in the definitions, but understanding the real difference between a SOC 2 Type 1 and Type 2 report comes down to one thing: proof. The entire gap between the two boils down to what an auditor actually examines and the evidence they demand. This difference in rigor is what gives one report so much more weight with your customers than the other.
A Type 1 audit is a design review. Think of it as an auditor checking the blueprints for your security program. They are verifying that your controls look good on paper at a single moment in time. They’re not stress-testing the foundation.

Type 1 Evidence: All About Documentation and Design
During a Type 1 audit, evidence collection is focused on your policies and configurations. An auditor is mostly looking at your documented intent.
They’ll typically ask for things like:
- Policy and Procedure Documents: Your information security policy, access control rules, and incident response plans.
- System Configuration Screenshots: Proof of your firewall settings or cloud security configurations.
- Architectural Diagrams: Visuals that show how data flows and where you’ve placed controls.
The bottom line is that a Type 1 audit confirms you have controls and that they are, in theory, designed properly. It validates your security posture on a specific day.
Type 2 Evidence: Proving Operational Effectiveness
This is where everything changes. A Type 2 audit is built to test the operational effectiveness of your controls over a period of time, usually 3 to 12 months. It’s not enough to have a good policy on the books; you have to prove you consistently followed it when it mattered.
This requires a much more rigorous and invasive evidence-gathering process:
- Sampling: Auditors will pull a sample of real-world events—like new hires, code changes, or security alerts—from your observation period to test if the control worked every single time.
- Log Analysis: They’ll dig into system logs, access records, and change management tickets to find hard proof that your team followed the procedures.
- Team Interviews: Your engineers and staff will be interviewed to confirm they actually understand and execute the security policies day-to-day.
A Type 2 audit doesn’t take your word for it—it demands empirical proof. This shift from reviewing documentation to testing real-world execution is why enterprise buyers in sensitive industries like FinTech and HealthTech insist on a Type 2 report.
Let’s look at a simple, real-world example that makes the difference crystal clear.
Real-World Example: Employee Offboarding
Imagine your company policy states that a departing employee’s system access must be fully revoked within 24 hours of their last day.
-
For a Type 1 Audit: The auditor would simply review your documented offboarding policy and checklist. If the procedure looks solid and covers all the right bases, you’re good to go. The evidence is the document itself.
-
For a Type 2 Audit: This is a completely different game. The auditor will request a list of every single employee who left during the 6-month audit period. From that list, they’ll select a random sample—say, five former employees—and demand hard proof (like system logs or deactivation timestamps) that each person’s access was actually terminated within that 24-hour window.
This distinction is what builds real trust. A Type 1 shows you have a plan. A Type 2 proves your plan actually works under pressure, which is precisely the assurance customers need. The level of detail also depends heavily on which of the five SOC 2 Trust Services Criteria you’ve chosen to include in your audit.
Comparing Timelines and Costs: A Practical Breakdown
Let’s get straight to it. The decision between a SOC 2 Type 1 and Type 2 report almost always boils down to two things: time and money. The differences here aren’t small—they represent two completely different levels of investment and commitment.
Think of it this way: a Type 1 report is a sprint. It’s designed to get a report in your hands fast to unblock a sales conversation. A Type 2, on the other hand, is a marathon. It demands sustained effort over several months to prove your security controls are not just designed well, but actually work day-in and day-out.
Unpacking the SOC 2 Timeline
The biggest single difference between the two reports is the Type 2 observation period. This is a mandatory window—usually 3 to 12 months—where an auditor watches your controls in action to collect evidence. A Type 1 audit has no such requirement, which is why it’s so much faster.
Here’s how the timelines typically break down:
- Type 1 Timeline (4-8 weeks): This is a quick, linear process. You’ll do a readiness assessment, fix any immediate gaps, and then the auditor reviews your documentation as of a single point in time. It’s a snapshot.
- Type 2 Timeline (8-18 months): This is a long-haul journey. It starts the same way—readiness and remediation—but then you enter the observation period. Only after that window closes can the auditor finalize their testing and issue the report.
The timeline directly impacts your sales cycle. A Type 1 can satisfy an urgent request from a prospect in weeks. A Type 2 demonstrates a long-term, verifiable commitment to security that larger enterprise customers often consider non-negotiable.
For a more granular look at each phase, check out our guide on how long a SOC 2 audit takes. The extended timeline for a Type 2 isn’t passive waiting; it requires active project management to make sure you’re collecting evidence consistently.
A Transparent Look at Audit Costs
Just as the timelines are worlds apart, so are the costs. The price of any SOC 2 audit depends on your scope, system complexity, and your choice of auditor. But the core difference in effort—a point-in-time review versus a months-long evaluation—creates a clear price gap.
The total cost isn’t just the auditor’s invoice. It’s a mix of hard and soft costs:
- Auditor Fees: This is your main external cost. It’s significantly higher for a Type 2 because of the hundreds of extra hours the auditor spends testing your controls over time.
- Internal Team Hours: Your engineers, security team, and HR staff will spend a ton of time gathering evidence and answering questions. This internal resource drain is substantially higher for a Type 2.
- Compliance Tooling: Many companies use platforms to automate evidence collection. This is another line item for your budget, and its value really shines during the long haul of a Type 2.
The numbers tell the story. A SOC 2 Type 1 audit generally runs from $10,000 to $30,000. In sharp contrast, a SOC 2 Type 2 audit starts around $30,000 and goes up from there.
This price difference is a direct reflection of the effort. A Type 1 audit might take 2-4 weeks of prep followed by another 2-4 weeks for the audit itself. A Type 2 requires 2-6 weeks of prep, a 6 to 12-month evidence collection period, and then 4 to 6 weeks for the final audit. This makes the Type 1 an accessible starting point for early-stage companies, while the Type 2 is a serious, ongoing investment for more mature organizations.
Which Report Do Your Customers Actually Demand?
The technical debate between SOC 2 Type 1 vs. Type 2 is interesting, but let’s be honest—the only question that really matters is: which report will help you close deals?
Your compliance strategy shouldn’t live in a vacuum. It needs to be a direct reflection of your go-to-market strategy. The answer isn’t found in audit theory but in the real-world expectations and risk tolerance of the customers you’re trying to win.
For an early-stage startup, a SOC 2 Type 1 can be a sales-closing machine. When that first big prospect’s security questionnaire lands in your inbox, having a Type 1 ready is often the difference between a stalled deal and a quick win. It proves you’re serious about security and have had your controls validated by a real auditor.
Speed is the name of the game here. A Type 1 lets you check a critical box in the procurement process, satisfying their initial due diligence and keeping the sales conversation alive. It signals that your security program has a solid blueprint, even if you haven’t proven it works over a long period.
The Startup Scenario: Unblocking That First Enterprise Deal
Picture this: a B2B SaaS startup with a fantastic product but zero security certifications. They’re deep in talks for their first six-figure contract, but the enterprise prospect’s procurement team slams on the brakes. The demand? A SOC 2 report.
- The Problem: The entire sales cycle is at risk. Waiting over a year for a Type 2 report is a non-starter; the deal will evaporate.
- The Solution: Go for a SOC 2 Type 1. It’s a pragmatic, fast path forward. The startup can nail this down in just 4-8 weeks, handing the prospect a formal, auditor-signed report that validates their security design.
- The Outcome: The deal is unblocked. The startup lands its first major customer, bringing in critical revenue and building market momentum. They can immediately start the observation period for their future Type 2 report without losing the sale.
In this context, the Type 1 report isn’t the destination; it’s a strategic bridge to revenue.
The Enterprise Expectation: When “Good Intentions” Aren’t Enough
The moment you start targeting mid-market and enterprise customers, especially in regulated spaces like FinTech or HealthTech, the conversation shifts entirely. For these buyers, a Type 1 report is often seen as little more than a statement of intent.
Their vendor risk management teams are trained to hunt for proof of operational effectiveness. They don’t just care about your security design on paper; they need to know if it actually works day in and day out. They are assessing the real-world risk of plugging your service into their critical operations.
Only a SOC 2 Type 2 report provides this historical evidence, making it a non-negotiable requirement for any mature security program.
“A Type 1 report tells me you have a security policy. A Type 2 report tells me your team actually follows it. During due diligence, we heavily discount a Type 1 because it offers no proof of execution. For any vendor handling our sensitive data, a clean Type 2 is table stakes.”
This CISO’s take highlights the brutal reality. For procurement teams at companies where a data breach means massive fines or reputational ruin, only a Type 2 gives them the assurance they need to sign on the dotted line.
The Scale-Up Scenario: Cracking the Healthcare Market
Now, think about a growing HealthTech company. They’ve successfully used a Type 1 to land their first few customers. Their new goal is to sell their platform to large hospital networks and insurance providers—organizations handling huge volumes of Protected Health Information (PHI).
- The Problem: Prospects in this market are governed by HIPAA and have incredibly stringent vendor security requirements. Their due diligence is ruthless and demands proof of sustained security practices.
- The Solution: The company has to level up and invest in a SOC 2 Type 2 audit. This means committing to a 6-12 month observation period where they consistently prove their controls for protecting PHI are working flawlessly.
- The Outcome: With a Type 2 report in hand, the company now meets the baseline security demands of the healthcare industry. This unlocks access to larger, more lucrative enterprise accounts that were completely off-limits before.
Ultimately, your customers’ demands should write your compliance roadmap. A Type 1 is a fantastic tool to accelerate early sales, but a Type 2 is the key to unlocking mature, high-value markets.
A Strategic Framework for Choosing Your SOC 2 Path
Deciding between a SOC 2 Type 1 and Type 2 report isn’t just a technical checkbox—it’s a critical business strategy decision. Your choice depends entirely on your immediate needs, long-term goals, and what your target market demands. This framework is designed to help you move past the definitions and connect your compliance efforts directly to your growth.
The decision really boils down to a few key business drivers: customer urgency, resource availability, control maturity, and your market position. How you balance these factors will tell you whether to go for a quick Type 1, commit to a full Type 2, or use a phased approach.
This flowchart maps out how to think through the decision when new deals and enterprise buyers are on the line.
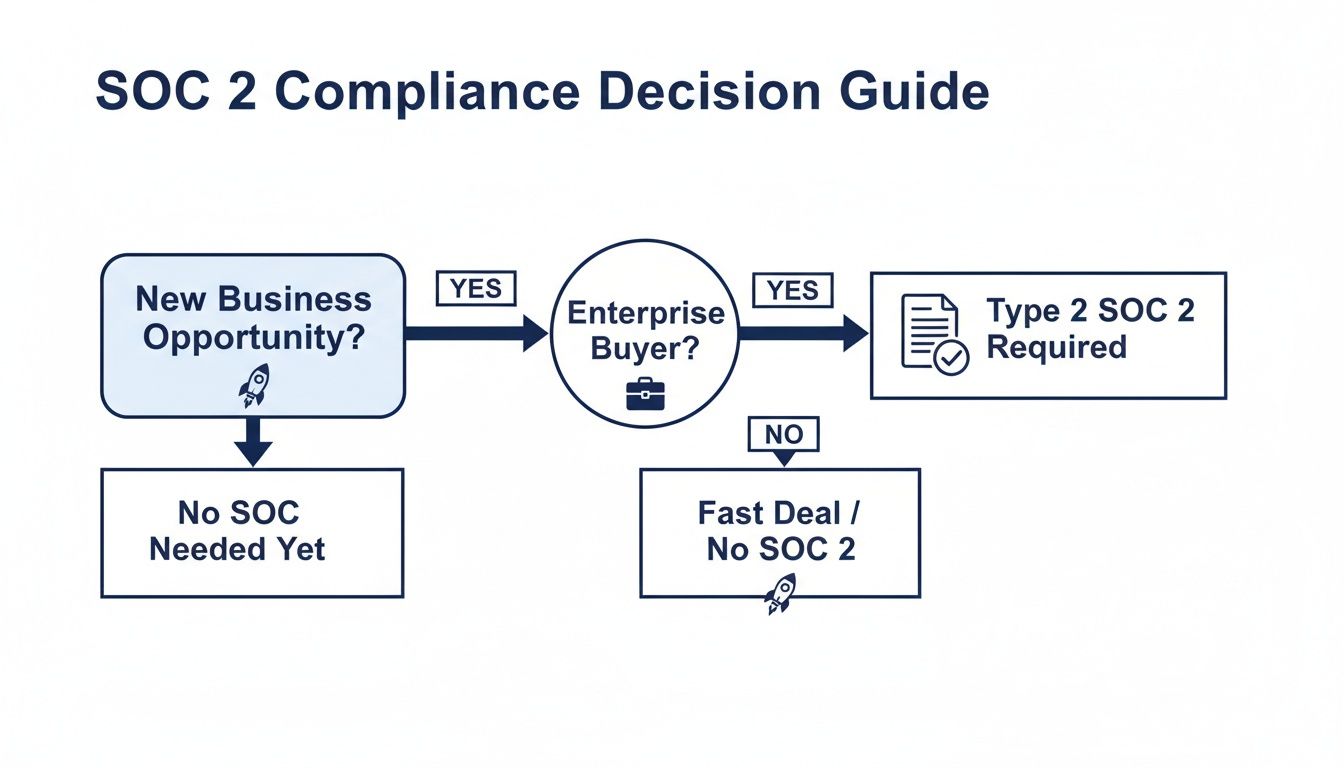
As the chart shows, the urgency of a deal often forces the decision, pushing companies toward a faster solution like a Type 1 report just to keep sales moving.
The Type 1 as a Strategic Stepping Stone
For many startups and growth-stage companies, using the Type 1 as a stepping stone is the most practical path forward. This strategy acknowledges the immediate reality of sales cycles while setting you up for the future demands of bigger customers. It’s a smart compromise between speed and rigor.
The idea is simple: you get a SOC 2 Type 1 audit first. With its shorter timeline—often just 4-8 weeks—you can get a formal, auditor-signed report into the hands of a prospect quickly. This is often enough to unblock deals, satisfy initial security questionnaires, and show you’re serious about security.
At the same time, the minute the Type 1 audit is done, you start the clock on the observation period for your SOC 2 Type 2 report. This phased approach lets you close near-term revenue without sacrificing the long-term credibility you’ll need.
This strategy effectively turns compliance into a sales enabler rather than a roadblock. You secure early wins with the Type 1 while methodically building the evidence needed for the Type 2 that will unlock more mature markets down the road.
This is a particularly strong move for companies that are still maturing their internal controls. The Type 1 process helps you formalize policies and procedures, creating a solid foundation for the much more intensive Type 2 audit. If you’re just getting started, our guide on SOC 2 compliance for startups offers a deeper dive into this early phase.
The Direct to Type 2 Approach
For more established companies or those targeting highly regulated industries from day one, going straight for a SOC 2 Type 2 report is often the right move. This path makes sense if your organization already has mature, well-documented controls and the resources to handle a longer audit process.
This strategy is usually a good fit for companies that meet a few key criteria:
- Established Control Environment: You already have solid security practices in place and can confidently prove they’ve been working over time.
- Enterprise-Focused Sales: Your main targets are large enterprises or clients in sectors like FinTech and HealthTech, who will ask for a Type 2 report right out of the gate.
- Resource Availability: You have the budget, team bandwidth, and tools to manage the sustained evidence collection needed for a 3-12 month observation period.
While this approach requires a bigger upfront investment of time and money, it immediately positions your company as a trusted, enterprise-ready partner. When mapping out your SOC 2 journey, looking at real-world examples like Tackle’s SOC 2 Type II certification can provide valuable perspective on the process and its benefits.
Use this framework to evaluate your business context and determine the most strategic SOC 2 path, whether it’s starting with Type 1, going directly to Type 2, or planning a phased approach.
Decision Framework: Which SOC 2 Report Is Right for You?
| Business Scenario | Recommended Report | Key Rationale |
|---|---|---|
| Early-stage startup with first enterprise deal on the line. | Type 1, then Type 2 | Get the report quickly (4-8 weeks) to unblock the deal, then begin the Type 2 observation period immediately. |
| Mid-market company selling to large enterprises with mature controls. | Direct to Type 2 | Your customers expect it, and you have the processes in place. A Type 1 won’t be enough to satisfy their due diligence. |
| Bootstrapped company with limited resources and no immediate SOC 2 demand. | Neither (yet) | Focus on building foundational security controls first. Begin the SOC 2 process 6-9 months before you anticipate needing it. |
| Company in a highly regulated industry (FinTech, HealthTech). | Direct to Type 2 | A Type 2 is table stakes in these sectors. Anything less will be a major competitive disadvantage. |
| Company that has just implemented many new security controls. | Type 1, then Type 2 | A Type 1 validates the design of your new controls, giving you a baseline before proving their effectiveness over time. |
| Company responding to an RFP that requires a SOC 2 report within 60 days. | Type 1 | It’s the only option that can meet an aggressive timeline. Communicate that a Type 2 is in progress. |
| Established company renewing its SOC 2 certification. | Type 2 (Annual) | Continuous compliance is the goal. Annual Type 2 audits demonstrate ongoing commitment and control effectiveness. |
This table helps translate your specific business situation into a clear, actionable compliance strategy. The key is to align your choice with your sales cycle and customer expectations.
Strategic Questions for Your Leadership Team
Getting alignment across your leadership team is crucial. Use these questions to drive a focused discussion and build consensus on the best path for your company.
- Sales & Revenue Impact: Are we at risk of losing deals right now because we don’t have a SOC 2 report? How urgent is the pain?
- Customer Profile: Who is our ideal customer today versus 18 months from now? What are their specific security requirements?
- Resource Constraints: Do we honestly have the internal team hours and budget to support a full Type 2 audit today?
- Control Maturity: How confident are we that our key security controls have been operating effectively for at least the last three months?
- Competitive Landscape: Do our main competitors have a Type 1 or a Type 2? How can we use our compliance to get an edge?
Answering these questions honestly will point you to the most logical path. Whether you choose a Type 1 as a quick-start solution or go directly to a Type 2, the decision should be a deliberate one that supports your company’s unique growth plan.
Frequently Asked Questions About SOC 2 Reports
Getting into the weeds of SOC 2 audits always brings up a few practical questions. Here are some straight answers to the things we hear most often, helping you get a better handle on the process, the reports, and what comes next.
Can I Fail a SOC 2 Audit and What Happens If I Do?
You don’t really “pass” or “fail” a SOC 2 audit. It’s not a test with a score. Instead, your auditor issues a professional opinion on your security controls. The best possible outcome is an “unqualified” opinion, which is auditor-speak for “everything looks great.”
But there are a few other possibilities:
- Qualified Opinion: This is like getting an A- instead of an A+. It means there are minor issues with one or two of your controls, but the rest of your system is solid.
- Adverse Opinion: This one stings. It means the auditor found significant, widespread problems with your security posture.
- Disclaimer of Opinion: This is rare, but it happens when the auditor couldn’t get enough evidence to form any opinion at all.
If you get anything other than a clean, unqualified opinion, the report will spell out the exceptions. Your team then has to write a management response explaining the problem and your plan to fix it. This is exactly why most companies do a readiness assessment before the audit kicks off—it lets you find and fix the gaps ahead of time, dramatically lowering the risk of a messy report.
How Do I Choose the Right Trust Services Criteria?
The only mandatory criterion is Security (often called the Common Criteria). This is the foundation of every SOC 2 report. The other four—Availability, Confidentiality, Processing Integrity, and Privacy—are optional.
So how do you choose? Simple: align them with the promises you make to your customers.
Think about your service commitments:
- Availability: Do your SLAs guarantee uptime? If you promise customers your service will always be up and running, you need this criterion to back it up.
- Confidentiality: Are you handling sensitive data like M&A documents, financial records, or intellectual property? This criterion proves you can keep a secret.
- Processing Integrity: Does your system perform critical calculations? Think financial processing, data analytics, or logistics. This shows your system is accurate, timely, and reliable.
- Privacy: Do you collect, store, or manage personal information (PII)? If you deal with customer data subject to regulations like GDPR or CCPA, the Privacy criterion is a must-have.
Don’t worry, you don’t have to decide in a vacuum. Your auditor will help you finalize the scope during the first few conversations to make sure your report is both relevant and valuable.
The criteria you choose aren’t just for checking a box. They’re a public statement about your operational promises. Getting them right makes your SOC 2 report a powerful tool for building specific, meaningful trust with your customers.
Does a SOC 2 Report Make Me GDPR or HIPAA Compliant?
No, a SOC 2 report is not a golden ticket to compliance with other frameworks like HIPAA, GDPR, or ISO 27001. Each of those frameworks has its own unique rules and requirements. For instance, HIPAA has very specific Security and Privacy Rules that have to be addressed on their own terms.
The good news? There’s a ton of overlap. Many of the security controls you build for SOC 2—like access management, data encryption, and incident response plans—are the very same things required by other regulations.
This means getting your SOC 2 can be a massive accelerator for other certifications. You can map your existing SOC 2 controls directly to HIPAA or GDPR requirements, which saves a huge amount of time and effort when you pursue those audits later. Some audit firms will even help you with this mapping.
How Long Is a SOC 2 Report Valid?
A SOC 2 report doesn’t have a hard expiration date stamped on it, but it definitely has a shelf life. In the real world, a report is generally considered “stale” after 12 months.
Here’s why:
- A SOC 2 Type 1 is a snapshot in time. A year later, customers will start asking if those controls are still actually in place and working.
- A SOC 2 Type 2 covers a specific window of time. Once you’re a year past the end of that window, its value starts to fade fast.
This is why SOC 2 isn’t a one-off project; it’s an ongoing program. To keep giving customers and prospects the assurance they need, most companies get a SOC 2 Type 2 audit every single year. It’s the only way to prove you’re committed to security for the long haul.
Finding the right auditor is one of the most critical steps in the SOC 2 journey. SOC2Auditors makes it simple by providing transparent data on pricing, timelines, and client satisfaction for over 90 firms. Stop the endless sales calls and get three data-driven matches tailored to your company’s needs. Find your ideal SOC 2 auditor today.