Difference Between SOC 1 and SOC 2 Reports for SaaS Companies

At its core, the difference between SOC 1 and SOC 2 reports is all about focus. SOC 1 audits controls over financial reporting, while SOC 2 audits controls related to data security and operations. Your choice boils down to a simple question: does your service directly impact your clients’ financial statements, or does it mainly handle their sensitive data?
SOC 1 vs. SOC 2: An At-a-Glance Comparison
Choosing the right compliance report is a critical business decision, and it’s easy to get them mixed up. Let’s clear the air.
A SOC 1 report is specifically for service organizations that could impact their clients’ Internal Controls over Financial Reporting (ICFR). Think of a payroll processing company—if they make a mistake, it directly affects their client’s financial statements. That client’s financial auditors will rely on your SOC 1 report to complete their own audit.
On the other hand, a SOC 2 report provides assurance about a service organization’s systems and data, built around the five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. This has become the go-to standard for most SaaS companies, cloud providers, and data centers that store or process customer information.

Core Distinctions and Use Cases
Here’s a simple analogy: SOC 1 is like an audit of a bank’s vault, ensuring all the financial assets are handled and reported correctly. SOC 2 is a comprehensive security assessment of the entire bank building, from its digital infrastructure and firewalls to its physical doors and cameras.
This distinction is fundamentally reshaping compliance strategies, with an estimated 85% of SaaS and FinTech firms now prioritizing one or both of these reports to win enterprise deals.
The scopes of these reports are intentionally different, forcing organizations to align their compliance efforts with what their customers actually need. Getting this right is the first step in selecting the right SOC audit services for your company.
The central question is: Does your service impact a client’s financial reporting? If yes, start with SOC 1. If you primarily handle or store customer data, SOC 2 is your path.
Key Distinctions Between SOC 1 and SOC 2 Reports
This table provides a scannable overview of the fundamental differences between SOC 1 and SOC 2 reports, helping you quickly grasp their distinct purposes and applications.
| Attribute | SOC 1 Report | SOC 2 Report |
|---|---|---|
| Primary Purpose | To report on controls relevant to a user entity’s financial reporting (ICFR). | To report on controls related to Security, Availability, Processing Integrity, Confidentiality, or Privacy. |
| Governing Standard | SSAE 18, Statement on Standards for Attestation Engagements No. 18. | AICPA’s Trust Services Criteria (TSC). |
| Main Audience | User entity’s management and their financial statement auditors. | User entity’s management, prospective customers, and business partners. |
| Typical Use Case | A payroll processing service or a collections management platform. | A cloud hosting provider, SaaS platform, or data analytics service. |
Ultimately, your customers and their auditors will tell you which report they need. But understanding these core differences empowers you to plan your compliance roadmap proactively instead of just reacting to sales requests.
Understanding the Core Purpose and Scope
To really get the difference between SOC 1 and SOC 2, you have to look past the similar names and focus on their core purpose. Each report is built to answer a completely different question for a very different audience, and that mission dictates everything from the scope to the evaluation criteria. One is all about financial integrity, the other is about operational security and trust.
A SOC 1 report is governed by the Statement on Standards for Attestation Engagements (SSAE) No. 18. Its purpose is laser-focused: to give a client’s financial auditors assurance about your internal controls that could impact their financial statements. It’s a direct plug-in for financial audits, like those required by the Sarbanes-Oxley Act (SOX).
Think of it as a critical link in a chain of financial trust. If your company processes payroll for another business, your internal controls—how you authorize payments, manage data, and secure financial information—directly affect the accuracy of your client’s books. Their auditors need your SOC 1 report to prove your part of the process is solid.
SOC 1: The Financial Assurance Report
The scope of a SOC 1 audit is tightly wound around Internal Controls over Financial Reporting (ICFR). It isn’t a broad review of your entire security program. Instead, the auditor only looks at the specific controls that could realistically impact a user entity’s financial statements.
For example, a SOC 1 audit for a billing platform might examine:
- Logical access controls over the systems that calculate and send invoices.
- Change management procedures for the software that processes financial transactions.
- Data processing controls ensuring all calculations are accurate and complete.
These control objectives are defined by the service organization itself, working with the auditor to address specific financial risks. This makes every SOC 1 report highly customized to the service, but always with the same end goal: preventing material misstatements in a client’s financial reports.
SOC 2: The Operational and Security Trust Report
A SOC 2 report, on the other hand, gives assurance about your systems and data from a much broader, operational point of view. Its job is to show that you have established—and are actually following—strict procedures to keep customer data safe and secure.
The scope of a SOC 2 is defined by the Trust Services Criteria (TSC), a set of principles from the AICPA. There are five in total:
- Security (Common Criteria): This is the mandatory foundation for every SOC 2 report. It covers the essential controls that protect information and systems from unauthorized access, disclosure, and damage.
- Availability: Are your systems available for operation and use as promised?
- Processing Integrity: Does your system process data completely, accurately, and on time?
- Confidentiality: How do you protect information that’s been designated as confidential?
- Privacy: This focuses on how you collect, use, retain, and dispose of personal information.
The crucial difference lies here: SOC 1 evaluates bespoke controls against financial risks, while SOC 2 measures an organization against a standardized set of security and operational criteria designed to build trust with a wide range of stakeholders.
While the Security criterion is always required, the other four are optional. This lets a company tailor its SOC 2 report to match its business promises. A cloud storage provider might focus on Security and Availability, while a healthcare data platform would almost certainly add Confidentiality and Privacy.
Since SOC 2 reports are all about data protection, a solid grasp of data security compliance principles is non-negotiable for a successful audit. This flexibility is what makes SOC 2 such a powerful tool for proving your operational integrity and data stewardship to customers, partners, and regulators, cementing its status as the go-to standard for modern tech companies.
Comparing Controls and Evaluation Criteria
This is where the rubber meets the road. The core difference between SOC 1 and SOC 2 really comes down to what the auditors are actually looking at. The two reports are built on entirely different foundations.
A SOC 1 audit is a bespoke review, tailored specifically to financial risks. A SOC 2 audit, on the other hand, measures your company against a standardized, industry-wide framework for security and operational controls. This distinction drives everything—the scope, the prep work, and the resources you’ll need.
SOC 1 Control Objectives: A Custom Financial Focus
For a SOC 1 audit, there’s no pre-written checklist. Your organization’s management team defines its own control objectives. These are custom statements that directly address how your service could impact a client’s financial reporting.
Think of it this way: you have to identify any process or system that could potentially cause a material misstatement in your client’s financial statements. Then, you design controls to prevent that from happening.
For instance, a cloud billing platform might create control objectives like these:
- Transaction Authorization: We have controls to make sure all invoices are generated from valid customer agreements and accurate usage data.
- Data Integrity: We have controls to ensure financial data is processed and stored completely and accurately within our platform.
- Logical Access: We have controls to restrict access to systems handling client financial data to authorized personnel only.
The auditor’s job is to test if these self-defined controls are designed properly (for a Type 1) and actually working as intended over time (for a Type 2). It’s a highly tailored approach that gives your clients’ financial auditors exactly what they need.
SOC 2 Evaluation Criteria: The Standardized Trust Services Criteria
SOC 2 works completely differently. Instead of you defining the objectives, your company is evaluated against a standardized framework called the Trust Services Criteria (TSC), which is created and managed by the AICPA. This provides a consistent benchmark for evaluating controls over systems and data.
The TSC is built around five categories. The first one is the foundation and is mandatory for every single SOC 2 report.
- Security (Common Criteria): This is the non-negotiable part of any SOC 2. It covers the fundamentals of a solid security program—things like risk assessments, access controls, system monitoring, and change management. It’s the baseline that proves you have a sound security posture.
The other four criteria are optional. You add them to your audit based on the services you provide and the promises you make to your customers. It’s vital to understand what each one covers, and you can dig deeper into the full SOC 2 Trust Services Criteria to see which ones make sense for your business.
Here’s how the other TSCs play out in the real world:
- Availability: This is for companies that promise a certain level of uptime or performance. An auditor would test your disaster recovery plans, performance monitoring, and network availability controls.
- Processing Integrity: If your service performs critical transactions or calculations (like a payment processor), this one is for you. The auditor checks that data is processed completely, accurately, and on time.
- Confidentiality: This applies if you handle sensitive business data that isn’t PII, like intellectual property or strategic M&A documents. The audit focuses on controls like encryption and access restrictions for that specific data.
- Privacy: This is different from Confidentiality. Privacy is all about protecting personally identifiable information (PII). The audit looks at how you collect, use, store, and dispose of PII, making sure it aligns with your privacy notice.
The core distinction is simple yet profound: SOC 1 evaluates bespoke, management-defined controls against specific financial risks, while SOC 2 measures an organization’s systems against a standardized set of security and operational criteria designed to instill broad customer trust.
This fundamental difference changes the game. With SOC 1, the heavy lifting is defining the right control objectives. For SOC 2, the challenge is implementing and documenting controls that map clearly to the AICPA’s predefined Trust Services Criteria.
Navigating Timelines and Report Types
Picking between a SOC 1 and SOC 2 report is only half the battle. The next critical choice is the report type, a decision that directly shapes your timeline, budget, and the level of assurance you can give your customers. Both SOC 1 and SOC 2 audits come in two flavors: Type 1 and Type 2.
Getting this right is essential for planning your compliance journey. One gives you a report in hand much faster, while the other delivers the deep, ongoing assurance that unlocks enterprise deals and builds lasting trust.
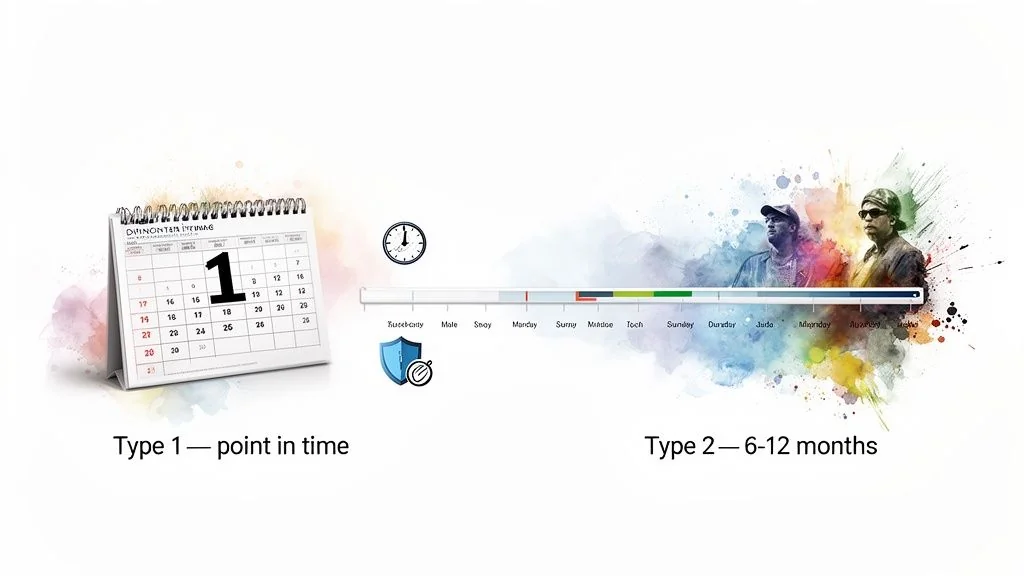
Type 1 Reports: The Point-in-Time Snapshot
Think of a Type 1 report as a photograph of your control environment on one specific day. It’s a point-in-time assessment. The auditor’s goal is to evaluate one key thing: the suitability of the design of your controls.
In practice, this means the auditor reviews your documentation, policies, and system architecture to confirm that, on paper, your controls are designed correctly to meet your objectives. They are not testing if those controls have actually worked over a period of time.
Because the scope is limited to design, getting a Type 1 report is a much faster process.
- SOC 1 Type 1 Timeline: You can typically get this done in 2 to 4 months. The focus on financial controls is often narrower, and these processes are usually well-documented already.
- SOC 2 Type 1 Timeline: This often takes a bit longer, usually around 3 to 6 months. The technical controls required by the Trust Services Criteria demand more extensive design and documentation work upfront.
A Type 1 report is a fantastic starting point for companies new to compliance. It’s proof that you’re serious about security and financial integrity, often enough to satisfy initial customer questions and get your foot in the door.
Type 2 Reports: The Gold Standard of Assurance
A Type 2 report is where the real proof lies. It goes much further, evaluating both the design and the operating effectiveness of your controls over a set timeframe, typically between six and twelve months. This isn’t a snapshot; it’s a feature-length film of your controls in action.
During this “observation period,” the auditor actively tests your controls to see if they’re working as intended, day in and day out. They’ll request evidence, interview your team, and perform sample testing to verify that your policies are being followed consistently.
This rigorous, long-term evaluation is precisely why a Type 2 report is considered the gold standard by enterprise clients. It provides a much higher level of assurance that your company doesn’t just have good policies—it actually lives by them.
A Type 1 report shows you have a blueprint for a fortress. A Type 2 report proves that the fortress has successfully withstood a year of siege tests. That’s the difference.
The timeline for a Type 2 report is a much bigger commitment. While a SOC 2 Type 1 might take up to 6 months to prepare for and complete, the more robust SOC 2 Type 2 audit process often stretches from 6 months to a year or more. This is because auditors are scrutinizing real-world performance over that extended observation period.
Making the Right Choice for Your Business
So, which type should you go for? The answer really depends on your immediate business goals, what your customers are asking for, and your available resources. Many companies take a smart, phased approach.
- Start with Type 1: Kick things off with a Type 1 report. It helps you establish a baseline of well-designed controls and can satisfy those urgent customer requests. You get a report in your hands faster and show you’re moving in the right direction.
- Transition to Type 2: The day you get your Type 1 report, start the clock on your observation period for a Type 2. This creates a seamless progression and demonstrates to customers that you’re committed to reaching the highest standard of assurance.
While a Type 1 report can open doors, it’s the Type 2 report that closes major enterprise deals. The effort is substantial, but the payoff in customer confidence and competitive advantage is undeniable. Understanding the nuances between a SOC 2 Type 2 vs Type 1 report is a critical first step in building a compliance roadmap for long-term success.
Choosing the Right Report: Real-World Scenarios
Knowing the technical differences between SOC 1 and SOC 2 is one thing. Applying that knowledge to your actual business—where the choice impacts sales, customer trust, and how you spend your time and money—is what really counts.
Let’s move past the theory. The decision boils down to the core function of your service. Do you directly touch the systems that power your clients’ financial statements, or are you primarily a custodian of their operational data? Answering that question is the first and most critical step.
When a SOC 1 Report is Non-Negotiable
A SOC 1 report becomes mandatory when your service is so deeply woven into a client’s financial operations that their own external auditors can’t sign off on their financials without getting assurance from you first. This is a common reality in FinTech and any B2B SaaS where financial data processing is the main event.
Think about these classic SOC 1 use cases:
- Payroll Processors: A company that calculates salaries, tax withholdings, and direct deposits has a direct, material impact on its clients’ financial reporting. One bug in your system could cause a massive financial misstatement for them.
- Accounts Receivable Automation: If your platform manages invoicing, collections, and revenue recognition for a client, you are integral to their financial health. Their auditors need proof that your processes are rock-solid.
- Trust Accounting Software for Law Firms: Any software that handles client funds held in trust is a critical piece of a law firm’s financial integrity. A SOC 1 proves that these sensitive transactions are handled correctly and ethically.
In every one of these situations, the primary audience isn’t your customer—it’s your customer’s financial auditor. They are relying on your SOC 1 report to verify the integrity of the data flowing from your service into their client’s books.
The real driver for a SOC 1 is external dependency. If your client’s financial auditors need to rely on your controls to form their own audit opinion, a SOC 1 report is the only way to provide that assurance.
Scenarios Demanding a SOC 2 Report
A SOC 2 report, on the other hand, is the go-to for a much broader range of technology companies. The need for a SOC 2 isn’t driven by financial auditors, but by customer and prospect demands for security, availability, and confidentiality. If your service stores, processes, or transmits sensitive customer data, a SOC 2 is almost certainly the right fit.
Here are a few examples of businesses where SOC 2 is table stakes:
- Cloud Service Providers (CSPs): Companies offering IaaS, PaaS, or SaaS depend on SOC 2 reports to prove their infrastructure is secure and reliable. It’s foundational for building trust.
- Data Analytics Platforms: A service that ingests and analyzes sensitive customer data has to demonstrate bulletproof controls over confidentiality and security. A SOC 2 is the standard way to provide this proof to enterprise clients.
- Customer Data Platforms (CDPs): These platforms are a goldmine of sensitive customer information, making robust security and privacy controls absolutely essential. A SOC 2 (often with Security, Confidentiality, and Privacy criteria) is frequently a deal-breaker in sales talks.
The Overlap: When You Might Need Both
So what happens when you do both? It’s more common than you think. Complex service providers, especially in the FinTech world, often find they need both a SOC 1 and a SOC 2 to keep different stakeholders happy.
Take a modern FinTech platform, for example. It might offer a service that automates a client’s payment processing (which screams SOC 1) while also hosting that sensitive customer financial data in the cloud (a classic SOC 2 use case). The SOC 1 assures financial auditors that transactions are handled properly, while the SOC 2 assures nervous customers that the platform itself is secure and highly available.
Before you pull the trigger on an audit, it’s smart to conduct a preliminary review to see where you stand. Reading a good guide to the gap assessment process can help you spot control weaknesses and clarify which compliance framework is the best match for your business.
Making Your Final Decision: A Strategic Framework
Choosing between a SOC 1 and SOC 2 report isn’t just a compliance task—it’s a strategic business decision. Get it right, and you build trust with the right audience, shorten your sales cycle, and turn a necessary expense into a competitive advantage. The best choice comes from looking inward at your services and outward at what your customers actually need.
To cut through the noise, the entire decision boils down to a few straightforward questions. Think of them as your guideposts, pointing you toward the report that matches your business model and the primary risks you manage for clients. A little honesty and clarity here will save you a ton of time and money down the road.
Core Questions to Guide Your Choice
Before you even think about talking to an auditor, get your team in a room and hammer out the answers to these questions. The right path forward almost always reveals itself.
-
Do our services directly impact our clients’ financial reporting? This is the big one. If your platform processes transactions, handles payroll, or manages any data that feeds directly into a client’s financial statements, the answer is a clear yes. This is a massive signal that you need a SOC 1 report.
-
Are customers constantly asking for security assurance or sending over lengthy questionnaires? When your sales conversations revolve around data protection, system uptime, and confidentiality, your customers are indirectly asking for a SOC 2 report. It’s the standard proof of security for nearly all SaaS and cloud service providers today.
-
What is the primary risk we manage for our clients? Be brutally honest. Is the biggest catastrophe a financial misstatement caused by an error in your service (a SOC 1 problem)? Or is it a data breach stemming from a security vulnerability (a SOC 2 problem)? Define the core value you deliver and the biggest disaster you prevent.
This simple decision tree helps visualize the fundamental difference and should make your choice pretty clear.
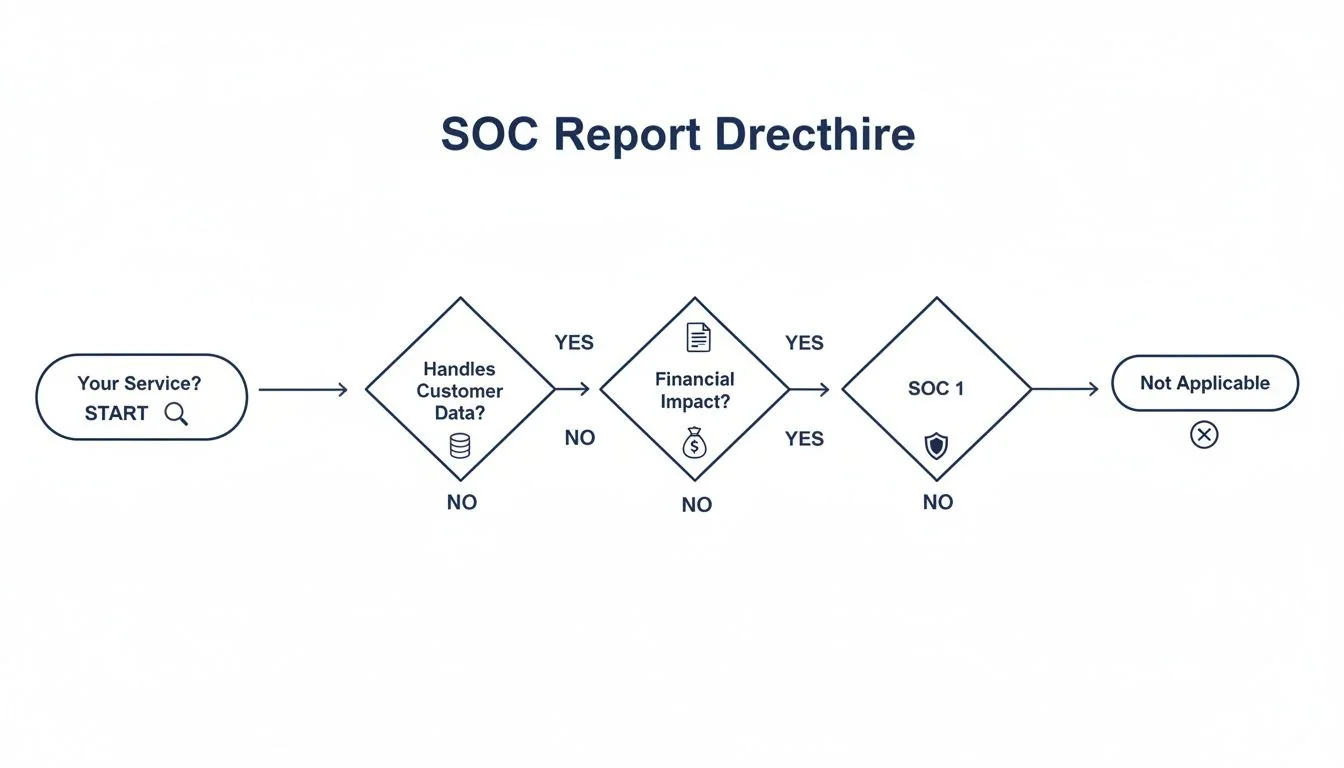
As you can see, the path to a SOC 1 report starts and ends with direct financial impact. For everything else related to handling sensitive customer data, the road leads to SOC 2.
Choosing the right report is the first step. But the second, equally critical step, is picking an audit firm that lives and breathes your chosen report type and industry. An auditor who gets your business can offer priceless guidance, making the process far smoother and the final report much more meaningful.
Ultimately, your decision should be a direct reflection of the promises you make to your customers. Whether you promise to protect the integrity of their financial data or safeguard their operational secrets, the right SOC report is your proof. It transforms compliance from a defensive chore into a proactive tool for building trust and winning bigger deals.
Common Questions, Answered
When you’re navigating the world of compliance, a few key questions always come up. Here are the straightforward answers you need.
Can I Use a SOC 2 Report Instead of a SOC 1?
No, you can’t. They’re built for entirely different purposes and audiences. A SOC 2 report is all about your controls related to the Trust Services Criteria—security, availability, and so on.
It simply can’t give your client’s financial auditors the assurance they need over your Internal Controls over Financial Reporting (ICFR). That’s the entire point of a SOC 1. If what you do touches a client’s financial statements, a SOC 1 is almost always going to be a hard requirement.
Which Report Costs More: SOC 1 or SOC 2?
While it always depends on the specifics, a SOC 2 report is generally more expensive. The reason is scope. The Trust Services Criteria often require a broader, more technical audit, especially if you add criteria like Availability or Confidentiality.
A SOC 1 is narrowly focused on financial controls, which can keep the cost down. But don’t assume it’s always cheaper—a complex financial service can easily drive up the price of a SOC 1 audit. Your best bet is always to get quotes based on your specific control environment.
The core reason for the cost difference is scope. SOC 2’s security focus often involves testing a larger, more technical set of controls across the organization, whereas SOC 1 is laser-focused on financial-related processes.
If I Have SOC 2, Do I Still Need ISO 27001?
This comes down to one thing: your target market. While SOC 2 and ISO 27001 have a ton of overlap in security controls, they are viewed very differently around the world. SOC 2 is the heavyweight champion in North America.
ISO 27001, on the other hand, is an internationally recognized certification for an Information Security Management System (ISMS) and is often the standard expectation in Europe and Asia. Many global companies end up getting both to cover all their bases. The good news is that doing one makes getting the other much, much easier.
Ready to find the right auditor for your compliance journey? SOC2Auditors helps you compare 90+ top firms with transparent pricing and real client feedback. Get three tailored matches in 24 hours without the sales calls. Find your perfect auditor.