If you’re new to the world of ISO, the difference between ISO 27001 vs ISO 27002 can be confusing. Let’s clear it up right away: ISO 27001 is the standard you get certified against. ISO 27002 is the detailed guidebook you use to get there.
Think of ISO 27001 as the “what”—a set of mandatory requirements for your Information Security Management System (ISMS). In contrast, ISO 27002 is the “how,” providing best-practice advice for implementing the security controls needed to meet those requirements.
Understanding The ISO 27001 And ISO 27002 Relationship
While they’re always discussed together, these two documents play distinct but complementary roles in your security program.
ISO 27001 is the management framework. It lays out the requirements for establishing, implementing, maintaining, and continually improving an ISMS. The core of the standard is in its mandatory clauses (Clauses 4 through 10), with a list of security controls found in Annex A.
ISO 27002, on the other hand, is a code of practice. It takes the high-level controls from ISO 27001’s Annex A and unpacks them with deep implementation guidance. It’s a catalog of generally accepted good practices that your teams can use to satisfy the requirements of the main standard.

Key Distinctions at a Glance
This symbiotic relationship is critical for any organization heading for certification. You can’t get certified for ISO 27002; it’s purely a supporting document. The audit is conducted against the requirements of ISO 27001.
However, auditors will expect to see that you’ve implemented controls thoughtfully and effectively—which is precisely what following ISO 27002 helps you do. The recent 2022 updates to both standards underscore this tight connection. ISO 27002:2022 streamlined its controls from 114 to 93, and this change was immediately reflected in the updated Annex A of ISO 27001:2022.
Here’s a simple analogy: ISO 27001 is the architect’s blueprint for a house. It specifies that you need walls, a roof, and plumbing—it’s what passes the final inspection. ISO 27002 is the detailed construction manual that explains the best techniques for framing those walls, laying the shingles, and connecting the pipes.
To make these differences crystal clear, here’s a quick side-by-side comparison.
ISO 27001 vs ISO 27002 At a Glance
The table below breaks down the fundamental differences in purpose, structure, and audience for each standard.
| Attribute | ISO 27001 (The ‘What’) | ISO 27002 (The ‘How’) |
|---|---|---|
| Primary Purpose | Defines requirements for an Information Security Management System (ISMS). | Provides a code of practice and implementation guidance for security controls. |
| Certification Status | Certifiable. Organizations are audited and certified against this standard. | Not certifiable. A supporting document offering best-practice advice. |
| Structure | Contains mandatory management clauses (4-10) and a list of controls in Annex A. | Details the implementation for each control listed in ISO 27001’s Annex A. |
| Audience | Management, GRC teams, and auditors who need to verify compliance. | IT and security teams responsible for implementing and managing controls. |
Getting this relationship right is the first step in any successful ISO certification journey. While they’re both part of the ISO 27000 family, they are absolutely not interchangeable. Many companies pursuing certification also look at other frameworks; you can explore the key differences between SOC 2 and ISO 27001 in our guide.
Breaking Down The ISO 27001 Management Framework
Now that we’ve established how ISO 27001 and ISO 27002 work together, let’s zoom in on ISO 27001. Think of it as the strategic constitution for your entire security program. It won’t tell you which firewall to buy or how to configure a specific server setting. Instead, it gives you a high-level, risk-based system for managing information security.
Here’s a common misconception: many people think Annex A is the most important part of the standard. It’s not. The real engine of ISO 27001 is found in its mandatory clauses—specifically Clauses 4 through 10. These sections lay out the requirements for establishing, implementing, maintaining, and continually improving your Information Security Management System (ISMS).
An ISMS isn’t just a binder on a shelf; it’s a living framework of policies, procedures, and controls that protect your company’s information. It’s a continuous program, not a one-and-done project. This is a critical distinction in the ISO 27002 vs ISO 27001 debate: ISO 27001 is for building the system, while ISO 27002 is for implementing the specific controls within that system.
The Mandatory Clauses Your Auditor Will Scrutinize
These seven clauses are the certifiable backbone of your security program. When an auditor shows up, their primary focus will be on whether you’ve effectively addressed each one. They provide a logical roadmap for building a resilient security posture from the ground up.
Let’s break down what each clause demands:
- Clause 4 Context of the Organization: You have to understand and document your company’s internal and external issues, plus the expectations of interested parties (think customers, regulators, and partners). This work defines the scope and boundaries of your entire ISMS.
- Clause 5 Leadership: This one is huge. It requires visible, demonstrable commitment from the top. Your leadership team must establish the information security policy, assign clear roles and responsibilities, and ensure the ISMS is woven into your actual business processes.
- Clause 6 Planning: This is where you get proactive about identifying security risks and opportunities. It involves conducting a formal risk assessment and creating a risk treatment plan—the foundation of your entire security strategy.
- Clause 7 Support: This clause covers all the resources you need to make the ISMS work. We’re talking about competence, awareness, communication, and documented information. It’s about making sure your team has the skills and tools to actually execute the plan.
An ISMS built on ISO 27001 is a top-down approach. Without genuine buy-in and active participation from leadership as required by Clause 5, the entire system is just a paper exercise. It will fail, regardless of how well individual controls are implemented.
The final clauses shift from planning to execution and improvement, which are essential for keeping your certification and adapting to new threats.
- Clause 8 Operation: This is where the rubber meets the road. You take the plans you made in Clause 6 and put them into action. You’ll execute your risk treatment plan and manage any changes to your environment in a controlled way.
- Clause 9 Performance Evaluation: You can’t manage what you don’t measure. This clause requires you to monitor, measure, analyze, and evaluate how well your ISMS is performing. This means conducting internal audits and formal management reviews to ensure everything is working as intended.
- Clause 10 Improvement: Based on what you find in Clause 9, you have to fix nonconformities and continually improve the ISMS. This “Plan-Do-Check-Act” (PDCA) cycle is what keeps your security posture evolving and relevant over time.
So, Where Does Annex A Fit In?
If the clauses are the engine, what is Annex A? Think of it as a reference catalog—a list of 93 security control objectives. Crucially, it is not an implementation checklist.
During your risk assessment (Clause 6), you’ll identify risks that need to be addressed. To treat those risks, you will select appropriate security controls. Annex A gives you a comprehensive menu to choose from. You then document which controls you’ve selected (and why) in your Statement of Applicability (SoA).
The SoA is a mandatory document that declares which Annex A controls you’re using and justifies any you’ve excluded. And this is exactly where the connection to ISO 27002 becomes crystal clear—that standard provides the detailed, practical guidance for actually implementing the controls you’ve selected from Annex A.
Unlocking The Practical Guidance Within ISO 27002
If ISO 27001 is the architectural blueprint for your Information Security Management System (ISMS), think of ISO 27002 as the contractor’s detailed instruction manual. It’s the playbook that turns high-level security goals into real-world, actionable tasks for your team. You can’t get certified against ISO 27002, but trying to implement ISO 27001 without it is like building a house with no instructions. It just doesn’t work.
The standard doesn’t invent new requirements. Instead, it unpacks each of the 93 controls from ISO 27001’s Annex A, giving you the why and the how for each one. This is the core of the ISO 27002 vs ISO 27001 relationship: one sets the requirement, the other shows you how to meet it.
A Modern Structure for Modern Threats
The standard got a major overhaul in 2022 to keep up with today’s security challenges. The updates to both ISO 27001 and ISO 27002 were a big deal—ISO 27002’s controls were streamlined from 114 down to 93. In the process, 58 were updated, 24 were merged, and 11 brand-new ones were added to address modern threats. This update, issued on February 15, 2022, also reorganized everything into four simple themes instead of the old 14 clauses. You can discover more insights about these changes on TrustCloud.ai.
This new structure makes implementation a lot more logical:
- Organizational Controls (37 controls): These are the foundational, high-level controls for your ISMS. Think policies, asset management, and how you handle suppliers.
- People Controls (8 controls): This section is all about the human element—security awareness training, remote work policies, and employee screening.
- Physical Controls (14 controls): This covers the protection of your physical stuff, like securing server rooms, equipment maintenance, and monitoring facilities.
- Technological Controls (34 controls): The biggest bucket, this provides the technical how-to for things like access control, encryption, secure coding, and network security.
This thematic approach makes it way easier for different departments—from HR to IT—to find the guidance that applies directly to them.
From Control Objective to Actionable Steps
Let’s make this real. Annex A has a control called 5.23: Information security for use of cloud services. In ISO 27001, that’s literally just the title. So, you know you need to secure your cloud services, but what does that actually mean? Where do you even begin?
This is where ISO 27002 shines. It takes that one-line objective and breaks it down into concrete steps, suggesting you should:
- Define Cloud Service Requirements: Figure out and document your specific security needs for any cloud service you use.
- Establish a Shared Responsibility Model: Clearly define who is responsible for what between you and the cloud provider.
- Implement Cloud-Specific Controls: Put security measures in place that are built for the cloud, which often look different from your on-premise solutions.
ISO 27002 bridges the gap between knowing what you need to do and understanding how to do it effectively. An auditor won’t just check if you have a control for cloud services; they’ll assess if that control is comprehensive and properly implemented, which is precisely what ISO 27002 helps you achieve.
This level of detail is exactly what you need to prove due diligence to an auditor. It shows you didn’t just check a box; you thoughtfully implemented a control that genuinely reduces risk. This focus on specific, verifiable actions is a key principle in other frameworks, too—you can learn more about defining a SOC 2 controls list, which follows a similar spirit of detailed implementation.
Bottom line: using ISO 27002 isn’t just a good idea; it’s the accepted best practice for bringing your Annex A controls to life.
Navigating The 2022 Updates And Their Impact
Information security never sits still, and neither do the standards that guide it. The 2022 updates to the ISO 27000 family were a massive step forward, dragging the framework into the modern threat landscape. These changes weren’t just a fresh coat of paint; they reflect a fundamental shift in how we should all be thinking about security.
The big headline was the consolidation of controls in ISO 27002. The old version listed 114 controls, which the 2022 revision smartly streamlined into a more logical set of 93. This wasn’t just about cutting the fat; many controls were merged for clarity, while others were beefed up to handle current tech and attacker tactics.
Even more important, the update rolled out 11 entirely new controls to plug security gaps that have become glaringly obvious in recent years. This is the ISO 27002 vs ISO 27001 relationship in action: as best practices get sharper in ISO 27002, the requirements in ISO 27001’s Annex A have to keep up.
A New Thematic Structure for Controls
Maybe the most practical change in ISO 27002:2022 was blowing up the old control layout. The previous model was spread thin across 14 clauses—a structure that felt clunky and academic. It’s been replaced by four clean, distinct themes, making the standard far more intuitive.
The new structure breaks down into four key areas: Organizational, People, Physical, and Technological.
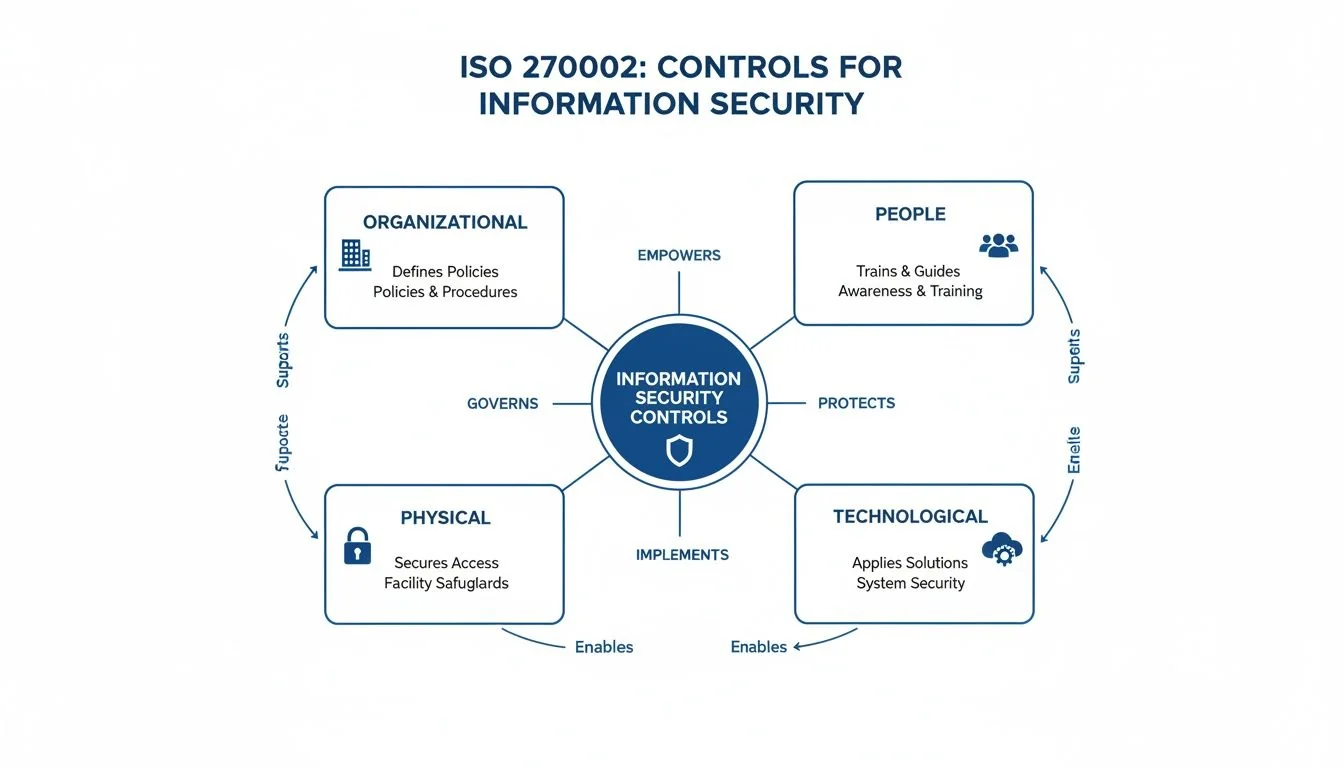
This new layout is a game-changer. It helps different teams—from HR to IT to facilities—quickly find and own the controls that actually matter to their daily jobs. No more digging through irrelevant clauses.
What Are the 11 New Controls?
The new controls are where the 2022 update really earns its keep. These additions zero in on modern security challenges that the old version just glossed over. They show a clear pivot toward proactive defense and the realities of today’s cloud-native world.
Here’s the new lineup:
- Threat intelligence: Actively hunting for and analyzing information about potential attacks.
- Information security for use of cloud services: Finally, a dedicated control for the messy reality of cloud risks and shared responsibilities.
- ICT readiness for business continuity: Making sure your tech can actually withstand a major disruption.
- Physical security monitoring: Using modern tools to watch over your physical spaces.
- Configuration management: Locking down secure configs for all your hardware and software.
- Information deletion: Securely nuking data when it’s no longer needed, for good.
- Data masking: Hiding sensitive data, especially in dev and test environments.
- Data leakage prevention: Using tech to stop sensitive data from walking out the door.
- Monitoring activities: Keeping a close eye on networks and systems for weird behavior.
- Web filtering: Blocking access to malicious websites before they can do damage.
- Secure coding: Building security into the development lifecycle from the start.
The introduction of controls like Threat Intelligence and Secure Coding signals a clear shift. ISO 27001 is no longer just about building defensive walls; it’s about embedding security into every process, from development to operations, and actively hunting for threats.
Mapping The Changes From 2013 to 2022
If you’re transitioning from the 2013 version, you absolutely need to understand how the old controls map to the new ones. Lots of familiar controls are still there, just hiding under a new number or merged with others. This mapping exercise is non-negotiable for updating your ISMS.
To give you a feel for how things have shifted, the table below shows a few key examples of how controls have been updated or consolidated. It’s a good snapshot of the new thematic thinking.
Mapping Key Control Changes From 2013 To 2022 Versions
| 2022 Control Theme | New 2022 Control Example (e.g., 5.23) | Corresponding Old 2013 Control(s) | Key Change/Improvement |
|---|---|---|---|
| Organizational | 5.23 Information security for use of cloud services | A.15.1.1, A.15.1.2, A.15.2.1 | Creates a dedicated control for cloud, addressing the shared responsibility model which was not explicit before. |
| People | 6.3 Information security awareness, education and training | A.7.2.2 Information security awareness, education and training | The control itself is similar, but its placement in the “People” theme provides better organizational context. |
| Technological | 8.16 Monitoring activities | A.12.4.1 Event logging, A.12.4.3 Administrator and operator logs | Merges several logging controls into a broader, more proactive “monitoring” control that emphasizes detection. |
| Technological | 8.23 Web filtering | New Control | Addresses a modern threat vector by adding a specific control for blocking access to malicious websites. |
The bottom line? A simple “lift and shift” of your old controls just won’t cut it. You have to get your hands dirty, review the new structure and content, and make sure your ISMS is truly aligned with current best practices. Anything less, and you won’t be ready for an audit against the ISO 27001:2022 standard.
Putting It All Together: A Real-World Scenario
Theory is great, but let’s see how this actually works in the wild. The interplay between ISO 27001 and ISO 27002 isn’t just academic; it’s a practical workflow that companies follow every day to get certified.
Imagine a fast-growing SaaS company we’ll call “InnovateTech.” They just landed their first huge enterprise client, but there’s a catch: the contract requires them to get ISO 27001 certified within 12 months. This is the perfect setup to see how the two standards work hand-in-hand.

Step 1: Laying the Foundation with ISO 27001
InnovateTech’s new CISO kicks things off with ISO 27001. This is their strategic blueprint for building out the company’s Information Security Management System (ISMS). Right now, it’s all about the “what”—defining the high-level framework for their entire security program.
They follow the mandatory clauses in ISO 27001 to get started:
- Define the Scope (Clause 4): They decide the ISMS needs to cover everything and everyone involved in building and running their core SaaS product. This scope gets formally documented and signed off by the leadership team.
- Get Leadership Buy-In (Clause 5): The CEO creates a formal information security policy, assigning the CISO the authority and resources needed to make the ISMS a reality.
- Assess Risk (Clause 6): The security team dives in and conducts a full risk assessment. A major risk jumps out immediately: insecure code being pushed to production could lead to a breach, violating their new client contract.
- Treat the Risk (Clause 6): To tackle that risk, they decide they absolutely must implement a secure software development lifecycle (SDLC).
This whole process culminates in their Statement of Applicability (SoA). Based on the risk they found, they select a handful of controls from ISO 27001’s Annex A, including the critical Control 8.28, Secure coding.
Step 2: Getting Tactical with ISO 27002
Okay, so the ISMS requires “secure coding.” The CISO can’t just walk over to the dev team and drop that on their desk. It’s not actionable. Developers need to know how to do it.
This is where ISO 27002 becomes their go-to instruction manual.
The head of engineering uses the specific guidance for Control 8.28 in ISO 27002 to draft a detailed Secure Development Policy. They go from a vague goal to a concrete, actionable checklist.
ISO 27001 points you to the destination—a secure application. ISO 27002 is the GPS giving you the turn-by-turn directions to get there, spelling out the specific tools, principles, and processes needed to write resilient code.
Using ISO 27002 as their guide, the team’s new policy now includes specific, practical requirements:
- Coding Principles: All developers must now follow standardized secure coding guidelines, like those from OWASP.
- System Security Testing: Static application security testing (SAST) tools are to be integrated directly into the CI/CD pipeline.
- Developer Training: The entire engineering department is now required to complete secure coding training every year.
- Separate Environments: They enforce strict rules to make sure production data is never, ever used in dev or test environments.
Without ISO 27002, InnovateTech would be guessing. They might implement a weak policy that an auditor would tear apart. While this process is specific to ISO 27001, the philosophy carries over to other frameworks. In fact, building a strong ISMS often gives companies a huge head start in understanding what is SOC 2 compliance and its control requirements.
This is the perfect synergy in action. ISO 27001 identified the risk and set the requirement, while ISO 27002 provided the expert guidance to meet that requirement effectively.
Your Action Plan for Nailing ISO 27001 Certification
Getting through an ISO 27001 audit can feel like a maze, but it’s actually a straightforward project once you know how to use both standards together. Success isn’t about choosing ISO 27002 vs. ISO 27001; it’s about using ISO 27002 as the instruction manual to implement the requirements of ISO 27001.
Think of it as a clear, step-by-step roadmap.

This plan is all about turning theory into action, guiding your organization toward a certification that actually sticks.
Your Certification Checklist
Here’s the logical sequence to take your project from kickoff to completion. Each step builds on the last, ensuring you create a comprehensive and—most importantly—auditable Information Security Management System (ISMS).
-
Get Leadership Buy-In (Clause 5): Seriously, start here. Your executive team needs to champion this, sign off on the information security policy, and put real budget and people behind it. Without this, your ISMS is dead on arrival.
-
Define Your ISMS Scope (Clause 4): Draw a clear line in the sand. Document exactly which departments, processes, locations, and assets the ISMS will cover. A fuzzy scope leads to a failed audit.
-
Run a Real Risk Assessment (Clause 6): This is the foundation of your entire security program. Identify the threats and vulnerabilities that could impact your information assets. The results of this assessment will directly dictate which controls you actually need to implement.
-
Create Your Statement of Applicability (SoA): Based on your risk assessment, you’ll select the necessary controls from Annex A. The SoA is the document where you list which controls you’re implementing and, just as crucially, justify any you’ve decided to exclude.
The SoA is one of the first things an auditor will ask for. It proves you’ve thoughtfully analyzed your specific risks instead of just blindly following a generic checklist.
-
Implement Controls Using ISO 27002: Now for the real work. For every single control you listed in your SoA, use the detailed guidance in ISO 27002 to implement it. This is the “how-to” phase where your team turns policy into tangible security measures.
-
Train Your People and Document Everything: Roll out security awareness training so everyone knows their role. At the same time, document every policy, procedure, and control you implement. If it isn’t written down, it didn’t happen.
-
Run an Internal Audit & Management Review (Clause 9): Before you call in the pros, audit yourself. Find and fix your own mistakes first. Follow that up with a formal management review to assess how the ISMS is performing against your objectives.
-
Kick Off the External Certification Audit: Once you’ve cleaned up the findings from your internal audit, you’re ready. It’s time to engage a certification body to conduct the formal Stage 1 and Stage 2 audits.
Frequently Asked Questions About ISO 27001 And ISO 27002
Even after you get the hang of how the standards work together, a few key questions always pop up. Getting these sorted out is crucial for avoiding expensive mistakes and frustrating delays on your path to certification.
Can I Get Certified in ISO 27002?
No, you absolutely cannot. This is one of the most important distinctions to remember.
ISO 27001 is the management standard that lays out the requirements for your Information Security Management System (ISMS). It’s the standard you get audited against and certified to.
Think of ISO 27002 as the official study guide, not the final exam. It’s a supporting document—a detailed code of practice offering implementation guidance for the security controls found in ISO 27001’s Annex A.
Is Using ISO 27002 Mandatory for ISO 27001 Certification?
Technically, no. But in reality, yes.
Attempting an ISO 27001 certification without constantly referencing ISO 27002 is like trying to build an engine without the blueprints. It’s not just a bad idea; it’s practically unheard of.
Auditors expect to see well-designed, comprehensive controls. Since ISO 27002 is the internationally accepted best practice, following its guidance is the clearest way to prove your controls are effective. Ignoring it means you’re just reinventing the wheel and hoping for the best.
An ISMS is the strategic framework (the “what” defined in ISO 27001), while the Annex A controls are the specific security measures you implement to reduce risk. The ISMS governs how you identify, manage, and improve security, while the controls are the tools you use to achieve your security objectives.
How Does the 2022 Update Affect Existing Certifications?
If your organization is currently certified under the older ISO 27001:2013 standard, you have a transition period—usually until late 2025—to update your ISMS to the new 2022 version.
This isn’t a simple paperwork exercise. You’ll need to map your existing controls to the new structure, implement and document the 11 new controls (like threat intelligence and secure coding), and overhaul your Statement of Applicability (SoA) before your next recertification audit.
Navigating compliance frameworks like ISO 27001 and SOC 2 requires choosing the right partners. SOC2Auditors provides a data-driven matching platform to help you find the perfect auditor for your needs, comparing real price ranges, timelines, and verified client feedback. Find your top three auditor matches in 24 hours at https://soc2auditors.org.