A SOC 2 risk assessment is a formal, documented process an entity uses to identify, analyze, and evaluate potential risks that could threaten the achievement of its service commitments and system requirements as defined by the AICPA’s Trust Services Criteria. This process is a foundational requirement for the Security principle, directly addressing criteria like CC3.1, which mandates that the entity identify risks to its objectives, and CC3.2, which requires the analysis and evaluation of those risks.
Understanding the Purpose of a SOC 2 Risk Assessment
For an organization pursuing SOC 2, the risk assessment is not an optional exercise; it is the primary evidence an auditor uses to verify that your security controls are relevant and purposefully designed. It serves as the strategic justification for your entire security program. Without a documented risk assessment, you cannot prove to an auditor that your controls are addressing specific, identified threats to the system, making it nearly impossible to satisfy the core requirements of the Security principle.
This process matters for SOC 2 because it answers the auditor’s fundamental question: “How did you decide which security controls to implement?” The risk assessment provides a documented, defensible answer, demonstrating that your security posture is based on a systematic analysis of threats rather than an arbitrary checklist. It is the mechanism that connects your company’s unique operational environment to the specific control requirements outlined in the SOC 2 framework.
Key Components in a SOC 2 Context
To build a risk assessment that satisfies SOC 2 audit requirements, you must structure it using concepts that align with the AICPA’s framework. An auditor expects to see a clear breakdown of risk into its core components:
- Threats: Potential events, whether internal (e.g., employee error) or external (e.g., cyberattack), that could adversely affect the achievement of your SOC 2 objectives.
- Vulnerabilities: Weaknesses in information systems, security procedures, internal controls, or implementation that could be exploited by a threat source. For example, an unpatched server or an inconsistent employee offboarding process.
- Impact: The potential negative consequences to the business if a threat exploits a vulnerability. In a SOC 2 context, this must be measured against your ability to meet service commitments related to security, availability, processing integrity, confidentiality, and privacy.
- Likelihood: The probability that a given threat will exploit a particular vulnerability.
Understanding how these components interrelate is critical for anyone pursuing SOC 2. Our guide on the broader process of a compliance risk assessment can provide additional context.
The goal of a SOC 2 risk assessment is to demonstrate a mature, repeatable process. An auditor wants to see a clear, logical line connecting an identified risk (e.g., an insider threat), your analysis of its potential impact on a Trust Service Criterion (e.g., Availability), and the specific control you have in place to mitigate it (e.g., role-based access control). For a deeper dive into the criteria your controls must satisfy, refer to the SOC 2 Trust Services Criteria.
Ultimately, your risk assessment creates the documented narrative that proves your security measures are not random but are thoughtfully designed to neutralize specific threats to the service commitments you make to your customers. This document is a cornerstone of your SOC 2 audit evidence. An auditor will request it early in the engagement, and its quality sets the tone for the entire audit.
How to Build Your Risk Register
The risk register is the central artifact for your SOC 2 risk assessment. It is the living document that provides auditors with tangible proof that you have a formal process for identifying, analyzing, and treating risks to your systems and data. This is not a simple inventory of fears; it is a structured log that must detail each risk, its potential impact and likelihood, the controls in place to mitigate it, and the planned response.
For someone pursuing SOC 2, this matters because the risk register is the primary piece of evidence examined to test compliance with the entire CC3.0 series (Risk Assessment) of the Common Criteria. An incomplete or poorly constructed risk register is a common cause of audit findings. The process of building it must be collaborative to ensure it accurately reflects the organization’s true risk landscape, as auditors will often interview personnel from different departments to validate its contents.
Facilitating Collaborative Risk Workshops
To create a comprehensive risk register that will withstand audit scrutiny, you must involve stakeholders from across the organization. Engineering, IT, operations, product development, HR, and legal all possess unique insights into potential threats and vulnerabilities. A risk identified by an engineer (e.g., a vulnerable open-source library) is just as critical for SOC 2 as one identified by HR (e.g., inconsistent access removal during employee termination).
Guide these workshops with specific, targeted questions that force concrete thinking relevant to SOC 2 objectives:
- Incident Post-Mortems: “Reviewing our last service outage, what was the root cause? What control weaknesses were exposed that could impact our Availability commitments?”
- System Architecture Review: “Looking at our data flow diagram, where is sensitive customer data stored, processed, and transmitted? What are the specific threats to its Confidentiality at each point?”
- New Feature Launches: “For the upcoming product release, what new third-party services are being integrated? What are the vendor risks to our Security and Availability criteria?”
- Process Mapping: “Walk me through the employee offboarding process. At what specific points could a former employee retain access, violating our controls for CC6.3 (Access Removal)?”
The specific, actionable outputs from these workshops form the basis of your auditable risk register.
This simple workflow shows how you turn those raw ideas into a structured assessment that auditors can follow.
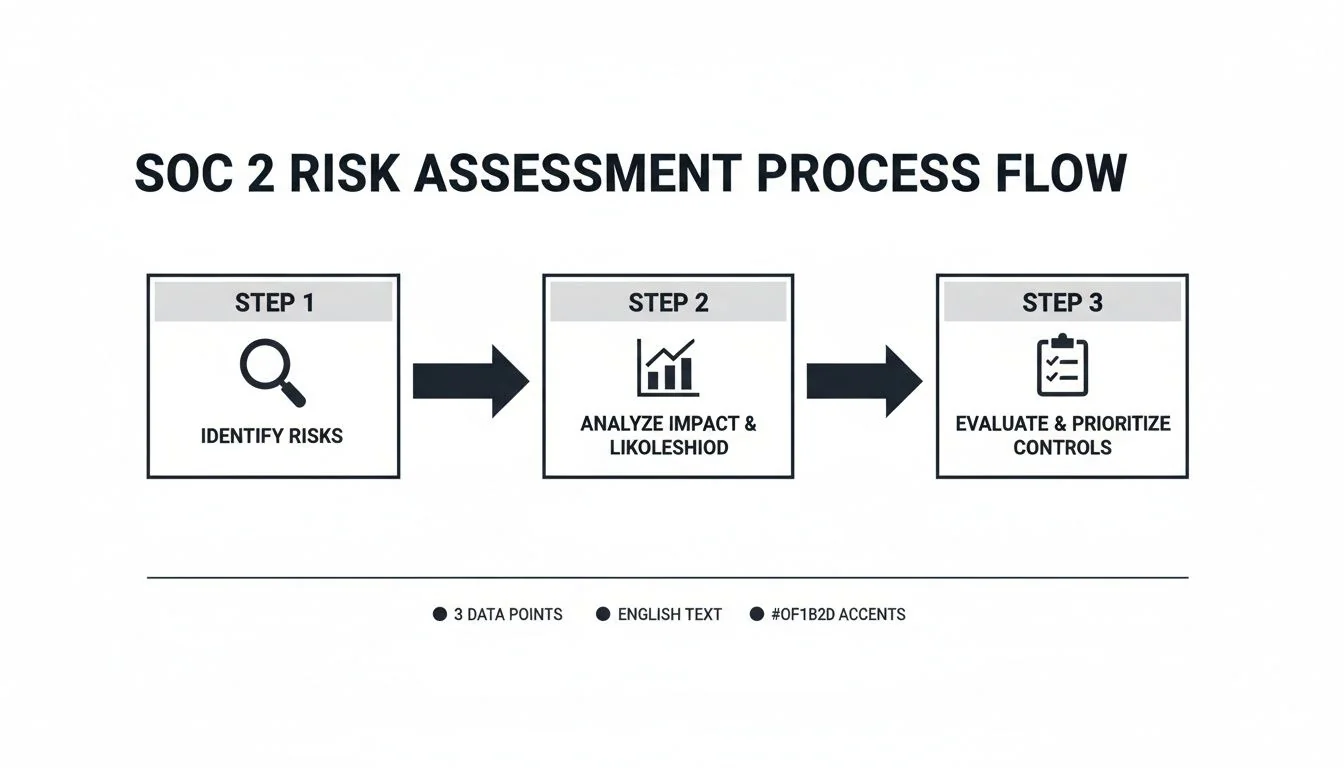
This journey is critical for SOC 2: identify a potential threat to a service commitment, analyze its potential impact and likelihood, and then evaluate the controls you have in place to mitigate it.
Scoring Risk with a Likelihood and Impact Matrix
Once you have identified a list of risks, you must analyze and prioritize them using a consistent, defensible methodology. A risk matrix is the standard tool for this. This matters for SOC 2 because auditors will test whether your risk analysis process is systematic and repeatable. A matrix provides objective criteria for scoring risks based on their likelihood and potential impact, moving the assessment from subjective opinion to quantifiable data.
Your matrix must be tailored to your business and its SOC 2 objectives. For a SaaS company, “impact” should be defined in terms of financial loss, reputational damage, operational downtime, and regulatory penalties related to failing service commitments. A common 5x5 matrix provides sufficient granularity for most organizations.
Here is a sample matrix you can adapt. It provides a structured way to assign scores and ensures a common language for evaluating threats.
Sample Risk Likelihood and Impact Matrix
| Score | Likelihood Level | Likelihood Description | Impact Level | Impact Description (e.g., Financial, Reputational, Operational) |
|---|---|---|---|---|
| 1 | Rare | Unlikely to occur in 5+ years | Insignificant | Negligible financial loss, no reputational harm, minor operational disruption. |
| 2 | Unlikely | May occur once in 3-5 years | Minor | Minor financial loss, slight reputational impact, brief service degradation. |
| 3 | Possible | May occur once in 1-3 years | Moderate | Moderate financial loss, noticeable reputational damage, partial service outage. |
| 4 | Likely | Expected to occur annually | Significant | Significant financial loss, widespread reputational harm, major service outage. |
| 5 | Almost Certain | Expected to occur multiple times per year | Catastrophic | Severe financial loss, long-term reputational crisis, complete service failure, regulatory action. |
Using this matrix is crucial for SOC 2 because it forces a structured, objective conversation that an auditor can follow.
A well-defined risk matrix is your best defense against subjectivity during an audit. It forces a structured conversation where a risk like ‘unauthorized access to a production database’ is clearly and objectively scored as having a catastrophic impact on the Confidentiality criterion, while a ‘minor cross-site scripting vulnerability’ might land at a low or moderate impact.
Understanding the real-world costs and timelines for a SOC 2 audit can help you define these impact levels. A typical audit can take two months for a prepared company but can easily stretch to 6 or even 12 months if you’re starting from scratch. Costs are just as significant, with Type I audits running $10,000 to $60,000 and Type II audits costing between $30,000 and $100,000. These numbers give you a tangible basis for scoring financial impact and justifying the resources needed to address high-priority risks. You can get more details on SOC 2 compliance costs and timelines at easyaudit.ai.
Articulating Risk with Clarity
How you describe each risk is critical for a SOC 2 audit. A vague entry like “Poor Security” is unauditable and will be rejected. Every risk statement must be specific and actionable, clearly defining the cause, the event, and the consequence in relation to your service commitments.
A strong risk statement follows this formula: [Threat Source] could exploit [Vulnerability], resulting in [Impact/Consequence on SOC 2 Objective].
Let’s look at the difference:
- Poor Example: “Server failure.”
- Good Example: “An external power grid failure could exploit our single-homed data center connection, resulting in a multi-hour service outage and violating our customer SLA for the Availability criterion.”
This level of detail matters because it creates a clear narrative that connects a potential threat directly to a SOC 2 objective, which is precisely what auditors are trained to test. Your risk register is the primary evidence that you are systematically managing threats to your service commitments.
Mapping Risks to Controls and the TSC
This stage is the most critical for anyone pursuing SOC 2. A risk register is merely a list of potential problems until you explicitly map each risk to the specific control(s) designed to mitigate it. This mapping process creates the core of your audit evidence, proving to an auditor that your security program is a deliberate, documented response to known threats and not just a collection of unrelated activities.
Without this explicit link, an auditor cannot validate your risk mitigation strategy. They need to see the direct connection between an identified risk, your internal control, and the corresponding Trust Services Criteria (TSC) to complete their testing procedures.
Connecting Risks to Practical Controls
Your goal is to demonstrate a defense-in-depth strategy where a single, high-impact risk is addressed by multiple controls. Auditors view this layering as a sign of a mature security posture. Your SOC 2 risk assessment template must have dedicated columns for “Control ID” and “Control Description” to document this mapping clearly.
Consider this common risk for a SaaS company:
- Risk Statement: A malicious actor could exploit an SQL injection vulnerability in our public-facing API to gain unauthorized access to sensitive customer data, resulting in a data breach that violates the Confidentiality criterion.
This matters for SOC 2 because you must now prove how you address this. You would map it to tangible controls:
- Control C-01: Web Application Firewall (WAF) is implemented and configured with rules to block common SQL injection patterns.
- Control C-02: All developers are required to complete mandatory secure coding training, with records maintained by HR.
- Control C-03: All application code that interacts with the database uses parameterized queries, as verified by code review checklists.
- Control C-04: The company conducts annual third-party penetration testing to proactively identify and remediate injection vulnerabilities.
Each control directly counters the risk. This layered approach provides a robust, defensible position during an audit.
Aligning Controls with the Trust Services Criteria
The final step is to link your internal controls to the specific AICPA Trust Services Criteria (TSC) they satisfy. This translates your operational security activities into the formal language of SOC 2 compliance, which is essential for the auditor’s report.
This matters because it provides the final piece of the evidentiary trail. It proves you are not just managing risk, but doing so in a way that directly meets the formal requirements of the SOC 2 framework.
Continuing with the SQL injection example, the mapping to the Common Criteria (the “CC” series) would look like this in your register. Our guide on the SOC 2 Common Criteria provides further detail on these requirements.
| Control ID | Control Description | Applicable Trust Services Criteria |
|---|---|---|
| C-01 | WAF implementation to block malicious traffic patterns. | CC7.1 - To meet its objectives, the entity uses detection and monitoring procedures to identify… changes to its information assets that may be indicative of threats. |
| C-02 | Mandatory secure coding training for developers. | CC2.2 - The entity provides for communication of information to appropriate personnel to support the functioning of internal control. |
| C-03 | Use of parameterized queries in all application code. | CC7.2 - The entity designs, develops, and implements control activities to mitigate risks. |
| C-04 | Annual third-party penetration testing. | CC7.1 - The entity uses detection and monitoring procedures to identify… vulnerabilities that are introduced into the entity’s systems. |
This three-way connection—Risk > Control > TSC—is the exact narrative an auditor follows during testing. When they select a risk from your register, they must be able to trace this clear, logical line to the SOC 2 criterion it helps satisfy.
The pressure to prove this is growing. Recent data shows that in 2025, 92% of organizations conducted at least two audits, with 58% conducting four or more. This makes a well-structured risk assessment template indispensable for continuous compliance. You can read more about these compliance trends and statistics on secureframe.com. This mapping process transforms your risk assessment from a simple internal tool into the strategic backbone of a successful SOC 2 audit.
Calculating Residual Risk and Defining a Treatment Plan
After identifying risks and mapping controls, the next step is to calculate residual risk—the level of risk remaining after your controls have been applied. This matters for SOC 2 because it demonstrates a mature understanding that no control is 100% effective. Acknowledging and quantifying residual risk shows auditors that your risk management process is realistic and continuous, which is a key attribute of a strong control environment.
This calculation is not just an academic exercise; it is the data that drives your risk treatment plan and justifies resource allocation for security improvements.

Calculating a Defensible Score
To calculate residual risk, you must first score the effectiveness of your existing controls. A simple 1-3 scale is sufficient and easy for auditors to understand:
- 1 - Highly Effective: The control is automated, preventative, and significantly reduces risk (e.g., automated vulnerability scanning that blocks deployments).
- 2 - Moderately Effective: The control is detective or procedural and relies on human action, offering a moderate risk reduction (e.g., annual security awareness training).
- 3 - Minimally Effective: The control has a minor effect, often due to inconsistent enforcement or being purely policy-based.
With an inherent risk score (Likelihood x Impact) and a control effectiveness score, you can use a simple formula like Residual Risk = Inherent Risk / Control Effectiveness. Documenting this methodology and applying it consistently across all risks is crucial for audit purposes.
Choosing Your Risk Treatment Strategy
Based on the calculated residual risk score, you must formally decide on a course of action. This is your risk treatment plan. This matters for SOC 2 because auditors will look for this documented plan to verify that you have a formal process for responding to identified risks, as required by criteria like CC3.2. There are four accepted strategies.
Your risk treatment plan is a direct response to your residual risk score. A high score demands mitigation, while a very low score may be acceptable. This documented decision-making is exactly what auditors look for to confirm you are actively managing your security program.
The table below breaks down the four strategies with examples relevant to a SaaS company undergoing a SOC 2 audit.
Risk Treatment Plan Options
| Treatment Option | Definition | Example Scenario for a SaaS Company |
|---|---|---|
| Mitigate | Implement new controls or improve existing ones to reduce the residual risk to an acceptable level. This is the most common response for high-priority risks. | A critical remote code execution vulnerability is discovered. The team decides to mitigate by deploying a new Web Application Firewall (WAF) and patching the vulnerable library immediately. |
| Accept | Formally acknowledge and accept the risk without taking further action. This is only appropriate for low-impact, low-likelihood risks where the cost of mitigation outweighs the potential loss. | A minor UI bug is identified that, under very specific and unlikely circumstances, could leak a non-sensitive internal version number. The team formally accepts the risk and adds it to the technical debt backlog. |
| Transfer | Shift the financial impact of the risk to a third party. This does not eliminate the risk itself but provides a financial backstop. | To manage the financial fallout of a major data breach, the company transfers a portion of the risk by purchasing a comprehensive cyber liability insurance policy. |
| Avoid | Discontinue the activity or process that is the source of the risk. This is the most drastic option, typically reserved for risks with unacceptably high impact. | A planned integration with a new, unvetted third-party vendor is found to have significant security flaws and no clear path to remediation. The company decides to avoid the risk by canceling the integration project. |
Documenting a treatment decision for every risk transforms your soc 2 risk assessment template from an analytical tool into an actionable plan. This provides powerful evidence that your risk management program is functional, directly supporting the Security (Common Criteria) principle and paving the way for a smoother audit.
Keeping Your Risk Assessment Alive and Breathing
For a SOC 2 audit, especially a Type 2, a static risk assessment created once and never updated is a significant red flag. It must be a living document. This matters because SOC 2 is not a point-in-time certification; it assesses the design and operational effectiveness of your controls over a period (typically 6-12 months). Auditors will specifically look for evidence that your risk assessment process is ongoing and adapts to changes in your business, technology, and threat landscape.
An outdated risk register fails to demonstrate this continuous management and can lead to a qualified opinion or finding. A core requirement of SOC 2 is to show that you are actively managing risk, not just documenting it once.
When to Drop Everything and Update Your Risks
Certain business events introduce significant new risks and require an immediate, ad-hoc update to your risk assessment. Waiting for a scheduled review is not sufficient for SOC 2 purposes.
Key triggers that demand an immediate review include:
- Major Architectural Changes: Migrating from a monolith to a microservices architecture introduces new risks related to API security, container vulnerabilities, and inter-service communication that must be immediately identified, assessed, and mitigated.
- Onboarding a Critical New Vendor: Integrating a new payment processor or data analytics platform introduces third-party risks. The SOC 2 process requires you to assess these vendor risks as part of your own, as per CC9.2 (Vendor Management).
- Learning from a Security Incident: A post-incident review that identifies a control failure (e.g., a successful phishing attack) must result in an updated risk assessment. The incident proves that a risk was either unidentified or its mitigation was ineffective, and auditors will expect to see this reflected in your register.
Setting a Formal Review Cadence
Beyond ad-hoc updates, you must have a formal, documented schedule for reviewing the entire risk register. For SOC 2, an annual review is the minimum requirement. However, for rapidly growing SaaS companies, a semi-annual or quarterly review demonstrates a more mature and proactive stance that auditors favor.
This review must be a formal meeting with the cross-functional team, and its output must be documented. The agenda should cover:
- Review of all existing risks for accuracy of likelihood and impact scores.
- Evaluation of the effectiveness of existing controls.
- Identification of new risks arising from business, technology, or threat landscape changes.
- Documentation of meeting minutes, attendees, and decisions made.
A documented annual review process is your primary evidence for satisfying the monitoring component of the COSO framework, which is the backbone of SOC 2. Your auditor will specifically ask for the meeting minutes or project tickets that prove you are actively overseeing and updating your risk management program.
The need for this diligence is growing. The SOC Reporting Services Market was valued at USD 5,392 Million in 2024 and is projected to reach USD 10,470 Million by 2030. A significant portion of that market, 44.99%, is dedicated to audit and compliance services, which directly fuels the need for continuous risk assessment methodologies. You can find more data about the growth of the SOC reporting market on marksparksolutions.com. This continuous process ensures your soc 2 risk assessment template remains a valuable, audit-ready tool that proves your commitment to ongoing security vigilance.
Using Your Risk Assessment for a Smoother Audit
Your completed risk assessment is the most important document you will provide during a SOC 2 audit. It serves as the central narrative for your entire security program, providing the documented rationale (“the why”) behind every control you have implemented. For someone pursuing SOC 2, this document is the bridge between your operational reality and the auditor’s testing procedures.
A well-structured risk assessment allows the auditor to quickly understand your security strategy, grasp your unique threat landscape, and see the logical connections you’ve drawn between risks, controls, and the Trust Services Criteria. This sets a collaborative and efficient tone for the entire audit engagement.
Presenting Your Risk Assessment to Auditors
When you provide your risk register to an auditor, you are giving them the blueprint they will use to scope their testing and guide their evidence collection. This is why the quality of this document is so critical for a smooth audit.
Do not simply email the file. Proactively walk the auditor through your methodology for identifying, scoring, and treating risks. Highlight one or two of your highest-rated risks and then demonstrate the layered controls you have implemented to mitigate them. This shows a command of your own security posture.
For example, you could highlight a high-impact risk like, “Unauthorized access to production database via compromised developer credentials.” Then, you can immediately show them the corresponding controls you have in place:
- MFA on all administrative accounts (Control maps to CC6.1)
- Principle of least privilege for database access (Control maps to CC6.3)
- Quarterly user access reviews (Control maps to CC6.3)
- Logging and alerting on failed login attempts (Control maps to CC7.1)
This immediately demonstrates a thoughtful, defense-in-depth strategy that is directly tied to SOC 2 criteria, building auditor confidence from day one.
Your risk assessment is your first and best opportunity to tell your security story. A clear, well-organized document shows the auditor you have a mature risk management process, which builds trust and dramatically reduces the back-and-forth questioning that can prolong an audit.
By proving you have a systematic approach to risk, you prove you’re not just “checking the box” for compliance. This is how you show your organization is built on a solid foundation of security—which is the entire point of the SOC 2 framework.
A meticulously maintained soc 2 risk assessment template is the primary evidence that proves your security program is deliberate, comprehensive, and directly aligned with the AICPA’s Trust Services Criteria. For any organization pursuing a SOC 2 report, demonstrating this level of diligence through the risk assessment process is the most direct path to streamlining the audit, minimizing requests for additional evidence, and achieving a clean audit opinion, which is the ultimate goal of SOC 2 audit readiness.
Finding the right auditor is the critical next step in your compliance journey. At SOC2Auditors, we replace the endless sales calls and confusing proposals with a data-driven matching platform. Get three tailored auditor matches based on your specific needs in 24 hours. Find your perfect auditor at https://soc2auditors.org.