So, what exactly is the SOC 2 certification process?
At its core, it’s a deep-dive audit where an independent CPA firm scrutinizes your company’s systems and controls. They measure everything against a set of principles—the Trust Services Criteria—defined by the AICPA. The whole thing wraps up in a formal report that proves you can securely handle customer data, covering things like Security, Availability, and Confidentiality.
But this isn’t just a technical hoop to jump through. It’s a massive business asset.
Why Your SOC 2 Certification Process Matters More Than Ever

Let’s be real: most fast-growing tech companies see SOC 2 as an expensive, time-sucking checkbox. It’s the project that always gets pushed to next quarter… until a huge enterprise prospect demands it to close a deal.
But looking at SOC 2 as just another compliance burden is a huge mistake.
Picture this: your SaaS company is in the final stretch of closing a landmark deal with a Fortune 500 client. The contract is drafted, your team is already celebrating, and then procurement slams on the brakes. The reason? One line item on their vendor security checklist: “Provide current SOC 2 Type 2 report.”
Suddenly, a process you thought was optional becomes the single biggest blocker to hitting your revenue target. This isn’t a hypothetical; it happens all the time.
A Strategic Asset, Not Just a Compliance Hurdle
When you start thinking of your SOC 2 audit as a sales and trust accelerator, the whole game changes. It stops being a reactive, painful cost center and becomes a proactive investment in your company’s future. A solid SOC 2 program tells the market you’ve reached a new level of operational maturity and that you take data security deadly seriously.
Getting a handle on the benefits of meeting security compliance helps put it all in perspective. This certification does way more than just check a box on a vendor questionnaire. It builds a foundation of trust that’s absolutely critical for long-term customer relationships, especially if you’re in sensitive industries like finance or healthcare.
A SOC 2 report is a narrative about your company’s commitment to security. It tells prospective customers that you have not only designed strong security controls but have also proven they work effectively over time.
The Foundation: The Five Trust Services Criteria
Every SOC 2 audit is built around the Trust Services Criteria (TSCs). This is the framework the auditor uses to evaluate your controls. We’ll get deeper into picking the right ones for your business later, but for now, you just need to know the five core principles that underpin the entire process:
- Security: This is the mandatory foundation for every single SOC 2 report. It covers how you protect information and systems from unauthorized access, breaches, and other threats. No skipping this one.
- Availability: This one is all about making sure your systems are up and running as promised in your Service Level Agreements (SLAs). If uptime is critical for your customers, you’ll want this.
- Processing Integrity: This assesses whether your system gets the job done right—is processing complete, valid, accurate, on time, and properly authorized? Think financial transactions or critical data jobs.
- Confidentiality: This applies to protecting specific information that’s been designated as confidential, like trade secrets or proprietary business plans. It’s about access control and preventing unauthorized disclosure.
- Privacy: This gets into the weeds of personal information—how you collect, use, store, disclose, and eventually dispose of it, all in line with your company’s privacy notice.
This guide will walk you through the entire SOC 2 certification process, from scoping your very first audit to keeping that compliance engine running smoothly year after year.
Defining Your Scope and Trust Service Criteria

Let’s be blunt: getting your scope right is the most critical part of the entire SOC 2 process. I’ve seen companies burn months of runway and tens of thousands of dollars auditing systems their customers couldn’t care less about. Define your scope too broadly, and you’re in for a world of pain. Scope it too narrowly, and that report you worked so hard for might be completely useless for the enterprise deal you’re trying to close.
This isn’t just a box-checking exercise. It’s a strategic decision that defines the boundaries of your audit. It answers one simple question: “What systems, people, and processes are we actually making promises about?”
Think of it like drawing a map for your auditor. Everything inside the lines gets put under a microscope. Everything outside is off-limits. That map has to perfectly match the service you sell and the commitments you make to customers.
Mapping Your Audit Boundaries
So, how do you draw this map? You start by identifying the absolute core components that deliver your service. This goes way beyond just your production servers; you need a holistic view of your entire service delivery ecosystem.
Typically, your in-scope components will include:
- Infrastructure: The cloud environments (like AWS, Azure, or GCP) and any data centers hosting your application and customer data.
- Software: The applications, databases, and internal tools that touch customer information in any way—processing, transmitting, or storing.
- People: The employees and key contractors with privileged access to sensitive systems. Think engineers, DevOps, and customer support staff.
- Data: The specific types of customer data your system handles. This will directly influence which Trust Service Criteria you’ll need later.
- Procedures: The documented operational playbooks that govern how you manage everything above, like your change management and incident response plans.
A rookie mistake is forgetting about the supporting cast. For instance, if you use a third-party ticketing system for customer support and it contains sensitive data, that system—and the people who use it—are almost certainly in-scope. As you figure this out, it’s crucial to understand the specific SOC 2 audit pentest requirements, as they can pull unexpected systems into your audit boundaries.
Selecting the Right Trust Service Criteria
Once your system boundaries are set, it’s time to choose your Trust Service Criteria (TSCs). The Security criterion is the foundation of every SOC 2 audit—it’s non-negotiable. The other four (Availability, Processing Integrity, Confidentiality, and Privacy) are selected based on your business model and the promises you make to customers.
Don’t fall into the trap of including all five just to look more secure. That approach adds a ton of complexity and cost to your audit for no good reason. You need to be strategic. You can learn more about how to select the right SOC 2 Trust Services Criteria in our detailed guide.
Choosing your TSCs isn’t about what makes your report look impressive. It’s about what accurately reflects your service commitments. An auditor will notice if you include a TSC that doesn’t genuinely apply to your operations.
To make the right call, think about these real-world scenarios:
- A telehealth platform that handles sensitive patient health information absolutely must prioritize Confidentiality and Privacy. Their customers need ironclad assurance that personal medical data is protected from any unauthorized disclosure.
- A data analytics service, where customers rely on it for critical business decisions, would lean heavily on Processing Integrity and Availability. They have to prove their platform is always online and that its calculations are spot-on.
- A cloud storage provider that puts 99.99% uptime in their SLAs had better include Availability. If they don’t, there’s a massive disconnect between their marketing promises and their audited controls, and customers will see right through it.
When you carefully define your scope and pick the right TSCs, you’re aligning your SOC 2 audit with your actual business goals. The final report becomes more than just a compliance doc—it’s a powerful tool for building trust and closing bigger deals.
Using a Readiness Assessment to Find and Fix Gaps
Think of the readiness assessment as a full-dress rehearsal for your actual audit. It’s hands down the most valuable investment you can make in the entire SOC 2 process. Its entire purpose is to shine a bright light on every weakness and control gap before your official auditor does.
Skipping this step is like trying to pass the bar exam without ever taking a practice test. It’s a gamble, and the odds are not in your favor.
This “pre-audit” mirrors the real thing, just without the high stakes of a formal opinion attached. You get a brutally honest look at how your controls stack up against the Trust Service Criteria you’ve chosen. What you walk away with is a detailed roadmap for remediation, turning a potentially chaotic process into a manageable, step-by-step project.
What Does the Assessment Actually Involve?
Don’t mistake a readiness assessment for a simple checklist. A good consultant or specialized CPA firm will go deep into your environment. They’ll interview key people, tear through your documentation, and scrutinize your technical configurations. They are laser-focused on finding any disconnect between what your policies claim you do and what’s actually happening on the ground.
For example, your employee offboarding policy might mandate that all system access is revoked within 24 hours of an employee’s last day. The readiness assessor will demand proof. They’ll want to see system logs or de-provisioning tickets from recent departures to verify that control is working. If they find an account that was still active a week later, that’s a gap.
This is exactly why the process is so critical—it uncovers the operational blind spots you’d never find on your own. We cover this in much more detail in our guide to the SOC 2 readiness assessment.
The point of a readiness assessment isn’t to get an A+. It’s to find every single problem so you can build a bulletproof remediation plan. A perfectly clean readiness report is actually a red flag that the assessment wasn’t thorough enough.
Interpreting the Gap Analysis and Building Your Plan
The main deliverable from the assessment is a gap analysis report. This document will list out every control that’s missing, broken, or not operating the way you think it is. It can be a sobering read, but it’s your blueprint for success. In fact, most assessments uncover gaps in an estimated 85% of cases, often needing one to three months of serious remediation work.
Your next job is to transform that report into an actionable plan. Don’t just treat it as a monster to-do list; you have to prioritize.
- High-Priority Gaps: These are the showstoppers. Think critical access control failures, a non-existent incident response plan, or a total lack of vendor security reviews. These are the things that would almost certainly lead to a qualified opinion, and they need to be fixed now.
- Medium-Priority Gaps: These are important but not catastrophic. Maybe your policy enforcement is inconsistent, or you have gaps in your employee security training records.
- Low-Priority Gaps: These are often procedural tweaks or documentation updates that can be handled over time.
Let’s say a fintech startup runs through an assessment and finds two major gaps. The first is a high-priority disaster: developers have standing, unaudited access to production databases. The second is a medium-priority issue: their vendor management process is completely ad-hoc, with no formal risk assessments for new software partners.
Their remediation plan would immediately prioritize implementing a just-in-time access control system for the database. In parallel, they’d start drafting and rolling out a formal vendor risk management policy. Showing up to your official audit with a documented plan that proves you’ve already fixed your biggest problems demonstrates real security maturity. It makes the entire audit smoother, faster, and a whole lot less stressful.
Choosing Your Auditor and Audit Type
Picking the right audit partner and report type is one of the most critical decisions you’ll make in the entire SOC 2 process. This choice directly shapes your budget, timeline, and ultimately, how your customers perceive your security posture. Don’t just Google “SOC 2 auditor” and pick the first or cheapest option—this is about finding a true partner for the long haul.
A great auditor does so much more than check boxes on a list. They should understand your industry, communicate clearly, and have real experience working with companies at your growth stage. The wrong firm can drag out the audit and turn it into a painful, bureaucratic nightmare. The right one, however, can make it a genuinely valuable exercise that improves your security.
Finding the Right Audit Firm for Your Business
Think of your auditor as more than just a vendor; they’re a key partner in proving your commitment to security. When you start evaluating firms, you need to look past the price tag and dig into what really matters for a smooth and effective audit.
Kick things off by asking about their specific experience in your niche. An auditor specializing in B2B SaaS will get your environment in a way that a firm working mostly with brick-and-mortar businesses never could. Don’t be shy about asking for references from companies that look like yours. You can also dive into our detailed breakdown of top SOC 2 audit firms to get a head start.
Here are a few key questions to guide your search:
- Industry Expertise: Have they audited other companies in your vertical, like fintech, health tech, or e-commerce?
- Communication Style: How do they actually manage the audit? Will you have a dedicated point of contact, or will you be fighting for attention?
- Company Stage Experience: Do they get the resource constraints and operational realities of a startup or a growing mid-market company?
Choosing an auditor is a long-term relationship, especially with annual Type 2 reports. Prioritize a firm that feels like a collaborative partner, not an intimidating interrogator. The goal is a productive audit, not a stressful one.
Type 1 vs. Type 2: Which Report Do You Need?
The single biggest decision you’ll make here is between a SOC 2 Type 1 and a Type 2 report. They serve very different purposes, and picking the right one comes down to your immediate business needs and long-term goals.
A SOC 2 Type 1 report is a “point-in-time” assessment. The auditor comes in and examines your controls on a specific date to confirm they are designed correctly. It’s faster and less expensive, making it a fantastic tool for companies that need to show compliance now to unblock a sales deal.
A SOC 2 Type 2 report is far more rigorous. It assesses the operational effectiveness of your controls over a period of time, usually 3 to 12 months. This is the gold standard that larger enterprise customers and mature organizations demand because it proves your security practices are consistently followed day in and day out.
To help you decide which path makes sense, this comparison table breaks down the core differences.
SOC 2 Type 1 vs Type 2 Report Comparison
| Attribute | SOC 2 Type 1 | SOC 2 Type 2 |
|---|---|---|
| Purpose | Assesses the design of security controls at a single point in time. | Assesses the operational effectiveness of security controls over a period of time. |
| Timeline | Faster. Typically completed in 4-8 weeks (after readiness). | Longer. Requires an observation period of 3-12 months, plus audit time. |
| Cost | Less expensive. Averages $20,000-$50,000 for startups. | More expensive. Averages $40,000-$150,000 for startups. |
| Customer Perception | Good for demonstrating initial commitment and unblocking sales deals. | The gold standard. Required by most enterprise customers and mature partners. |
| Effort | Lower internal effort focused on documentation and design. | Higher internal effort requiring ongoing evidence collection and monitoring. |
| Best For | Startups needing a report quickly to close a deal or prove security intent. | Companies selling to enterprise clients or needing to provide the highest level of assurance. |
In short, a Type 1 report gets you in the game quickly, while a Type 2 report proves you can stay there.
This decision tree can also help you visualize the path from identifying the need for SOC 2 to kicking off the readiness and audit process.
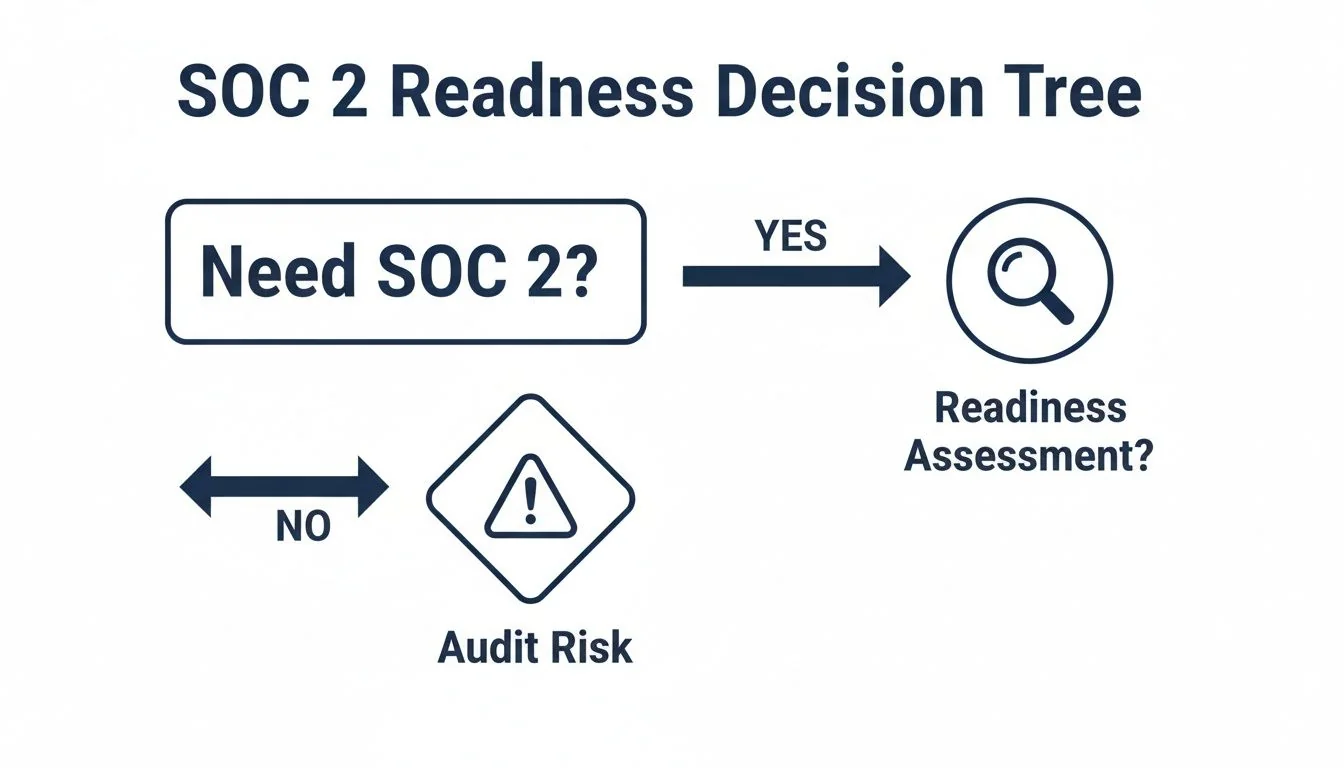
As the chart shows, a readiness assessment is the smartest first move for any company serious about compliance. It helps you avoid the significant risk—and cost—of walking into a formal audit unprepared.
A Practical Strategy for Startups
Let’s walk through a common scenario. A fast-growing startup gets an urgent request from a huge potential client. The catch? They require a SOC 2 report to sign the contract, and the sales team is promising the deal will close this quarter. Waiting 6-12 months for a Type 2 report just isn’t an option.
This is the perfect use case for a strategic, two-phase approach. The startup can immediately hire an auditor to pursue a Type 1 report. This can often be wrapped up in just a few months, satisfying the client’s immediate request and getting that critical deal across the finish line.
At the same time, they start the clock on the official “observation period” for their Type 2 report. By the time their next annual audit cycle comes around, they’ll have the required 6-month observation period under their belt. They can then seamlessly transition to the more robust Type 2, ready to take on even larger enterprise clients without missing a beat. This strategy perfectly balances short-term needs with long-term compliance maturity.
Navigating Fieldwork and Evidence Collection
Alright, this is where the rubber meets the road. After months of prep work, scoping discussions, and fixing gaps, the audit fieldwork officially kicks off. This part of the SOC 2 process can feel like a fire drill, but if you’re organized, it’s more like a well-rehearsed project than a chaotic scramble.
Your mission here is simple: make it dead easy for the auditor to find what they need, test your controls, and sign off on your report.
I always tell clients to think of themselves as a tour guide for their company’s security program. You’ve spent months building this amazing attraction, and now you’re leading the inspector through it, pointing out all the safety features and explaining exactly how everything works. A smooth tour always leads to a happy inspector.

Demystifying Evidence Requests
First things first: your auditor is going to send you a list of evidence requests. Don’t be shocked if it has hundreds of items. These aren’t vague suggestions—they are highly specific demands for proof that your controls are actually working the way you said they would. Responding efficiently is the name of the game.
Most of the evidence you’ll gather falls into a few key buckets:
- Documentation: This is your foundation. Auditors will want to see your information security policy, incident response plan, employee handbook, and other core governance documents.
- System Configurations: Get ready to take a lot of screenshots. You’ll need to prove how your cloud environment is set up—think IAM role permissions in AWS, firewall rules, or even GitHub settings that enforce pull request reviews before merging code.
- Procedural Evidence: This is proof that you actually follow your own rules. Real-world examples include signed offer letters with background check clauses for new hires, completion logs from your security awareness training platform, and spreadsheets showing your quarterly user access reviews.
- Sampling: For a Type 2 audit, the auditor won’t check everything. Instead, they’ll pick a sample of events that happened during your observation period. For instance, they might ask for all the onboarding paperwork for 5 specific new hires or the full change management trail for 10 specific code changes to verify your process was followed every single time.
Pro Tip: Don’t just dump a folder of raw data on your auditor and make them hunt for things. That’s a rookie mistake. Organize your evidence so it directly maps to their request list. A simple, clean folder structure like
CC6.1-Access-Control/can eliminate hours of frustrating back-and-forth emails.
Organizing Your Evidence for a Smooth Audit
How you manage this mountain of information will make or break your audit’s efficiency. A messy, disorganized evidence locker screams chaos and signals to the auditor that your internal processes might be just as sloppy. You’ve really got two paths here.
Lots of companies, especially first-timers, go the manual route with a meticulously organized shared drive (like Google Drive or SharePoint). They’ll create a master folder for the audit, with subfolders for each control family (CC1, CC2, etc.). This can work, but it requires a ton of discipline and manual effort to keep everything straight.
The other path is using a compliance automation platform like Vanta or Drata. These tools are built for this exact scenario. They integrate directly with your tech stack to automatically pull evidence—like screenshots of cloud settings or logs proving a new user was provisioned correctly. This doesn’t just save hundreds of hours of mind-numbing work; it gives both you and your auditor a central dashboard to track progress in real-time.
Preparing Your Team for Auditor Interviews
Evidence collection isn’t just about documents and screenshots. Your auditor will absolutely want to talk to your team. These interviews and walkthroughs are their chance to hear directly from the people who actually operate the controls day-to-day.
Your engineers, DevOps team, and HR staff need to be ready. They don’t need to become SOC 2 experts overnight, but they do need to confidently explain their daily processes as they relate to security. For example, an engineer should be able to walk the auditor through your entire change management process, from opening a Jira ticket and creating a pull request all the way to deployment.
The single most important thing you can do here is to anoint a single point of contact (SPOC) for the audit. This is usually a project manager or a technical lead who acts as the central hub for all communication. Instead of the auditor having to chase down five different people for five different things, they have one person to go to. This simple move streamlines the entire fieldwork phase and makes the audit experience immeasurably better for everyone involved.
You’ve got the SOC 2 report. Pop the champagne, right? Not so fast.
Getting that report in hand isn’t the finish line. It’s the starting gun for your real, ongoing commitment to security. This is the moment your focus has to shift from a temporary project to a permanent program. It’s what separates the companies that get security from those who just check a box.
First things first: you need to understand what your report actually says. Your auditor will issue an opinion, and this single paragraph is what every customer, prospect, and partner will zoom in on. It’s the final grade, and it completely dictates how that report lands in the market.
Understanding Your Audit Opinion
There are a few ways this can go, and each one tells a very different story about your security posture. Knowing the difference is critical for talking to prospects and for your own internal planning.
-
Unqualified Opinion: This is the gold standard. A clean bill of health. It means the auditor reviewed your controls and found no significant issues. You did what you said you would, and it works. This is what you’re aiming for.
-
Qualified Opinion: This is a mixed bag. It means the audit was mostly successful, but the auditor found a significant problem with one or more specific controls. It’s not a deal-breaker for everyone, but it’s a red flag you’ll have to explain to any savvy customer.
-
Adverse Opinion: This is the worst-case scenario. It means the auditor found widespread, material problems with your security controls. In short, your systems don’t meet the SOC 2 criteria. An adverse opinion will stop deals in their tracks.
An unqualified opinion isn’t just a passing grade; it’s a sales tool. It lets your team proactively share the report as hard proof of your security commitment, turning a compliance headache into a real competitive advantage.
Building Your Continuous Compliance Program
With the report in hand, the real work begins. A SOC 2 report is just a snapshot in time; continuous compliance is the year-round effort that makes sure your next audit is a breeze instead of a fire drill.
This isn’t about creating more work. It’s about baking security into your company’s DNA.
Your ongoing program should lock in a few key habits:
-
Annual Risk Assessments: At least once a year, you need to sit down and formally re-evaluate the threat landscape. What’s new? Did you launch a new product? Enter a new market? This process should directly inform your security roadmap for the next 12 months.
-
Ongoing Control Monitoring: Don’t wait for your next audit to find out a key control has been broken for six months. You need to be monitoring things constantly. This means running quarterly user access reviews, setting up automated alerts for cloud misconfigurations, and performing regular vulnerability scans.
-
Security Awareness and Training: Your team is always your first line of defense. A continuous program makes sure security isn’t a one-and-done onboarding video but an ongoing conversation through things like phishing simulations and monthly security reminders.
When you treat SOC 2 as a cycle, not an event, you build a genuinely resilient security culture. That’s what actually earns long-term customer trust and helps you grow faster.
Common Questions About the SOC 2 Process
Even the most detailed plan runs into real-world questions. Here are the straight answers to the things teams always ask when they’re staring down their first SOC 2 audit.
How Long Does This Actually Take?
Let’s be realistic: for a first-time audit, you should budget 6 to 12 months from start to finish. This is not a project you can cram into a single quarter.
Here’s how that time typically breaks down:
- 1-3 months for the initial deep dive—scoping out what’s in play and running a readiness assessment to see where you stand.
- 2-3 months for remediation. This is the heads-down work of actually fixing the gaps you just uncovered.
- 3-6 months for the observation period, which is the minimum window your auditor needs to see your controls working for a Type 2 report.
- 4-6 weeks at the end for the auditor to do their thing—fieldwork, testing, and writing the final report.
Trying to rush this is one of the most common mistakes we see. It almost always leads to a qualified opinion (the bad kind) or even an outright failure. Plan accordingly.
What Are the Biggest Hidden Costs?
The auditor’s invoice is just the tip of the iceberg. The number that usually shocks people is the internal cost.
The most significant hidden cost is almost always the time your own team will spend on this. Expect key people from engineering, ops, and HR to sink hundreds of hours into readiness, digging up evidence, and sitting in interviews with the auditor.
Beyond your team’s time, other major costs include:
- Compliance Automation Software: Platforms like Drata or Vanta can run you $7,000-$20,000+ per year. They’re not cheap, but the hours they save on evidence collection are often worth every penny.
- Remediation Tools: Your readiness assessment might reveal you need to buy new tools to plug security holes. This could mean investing in things like endpoint detection and response (EDR) software or new vulnerability scanners.
Can We Do This Without a Dedicated Compliance Person?
Absolutely. In fact, most startups and smaller tech companies don’t have a full-time compliance hire.
Typically, the responsibility gets split between a technical leader (like the CTO or a lead engineer) and someone on the operations side. The key is to officially name a single “SOC 2 project owner.” This person’s job is to keep the train on the tracks—they coordinate with the auditor, chase down tasks, and make sure deadlines are hit.
If you’re going this route, using a compliance automation platform isn’t just a nice-to-have; it’s essential for providing the structure and guidance your team will need.
Finding the right auditor is one of the most critical steps in the SOC 2 process. SOC2Auditors helps you compare 90+ verified firms based on real pricing, timelines, and client satisfaction scores. Get three tailored, objective auditor matches in 24 hours without the sales calls at https://soc2auditors.org.