A Practical Guide to soc2 compliance for Tech Companies
SOC 2 compliance isn’t just another technical checkbox to tick. Think of it as a powerful business asset that proves—with independent verification—that you’re a responsible steward of your customers’ data.
It gives your customers, especially the big ones, the confidence that their sensitive information is actually safe with you.
Why SOC 2 Is a Business Imperative

So, what is it? At its core, SOC 2 is a voluntary compliance standard for service organizations, developed by the American Institute of Certified Public Accountants (AICPA). It’s built around five key principles known as the Trust Services Criteria.
But just calling it a “standard” misses the point entirely. In today’s market, achieving SOC 2 compliance is one of the most effective levers for growth, especially for tech companies. It’s the difference between being a startup that says it’s secure and one that can prove it with a third-party audit report.
This proof is absolutely critical. For many tech companies, a SOC 2 report isn’t just a nice-to-have; it’s a make-or-break requirement for landing major deals and building a sustainable business. Let’s break down why.
Why SOC 2 Is a Business Imperative
| Business Driver | Key Benefit |
|---|---|
| Enterprise Sales Enablement | Unlocks deals with large corporations that list SOC 2 as a non-negotiable vendor requirement. It gets you past procurement and security reviews. |
| Building Customer Trust | Provides tangible, third-party assurance that you have robust controls in place to protect sensitive data, moving beyond simple marketing claims. |
| Competitive Advantage | When prospects are comparing you against a competitor, a SOC 2 report signals maturity and reliability, often becoming the deciding factor that closes the deal. |
| Operational Discipline | The process forces you to build and maintain a strong security posture, reducing risk and improving internal processes long-term. |
Ultimately, a SOC 2 report answers the fundamental question every enterprise customer has: “Can I trust you with my data?” A clean report is a definitive “yes.”
A Framework for Security Excellence
Unlike rigid, one-size-fits-all frameworks, SOC 2 gives you flexibility. It provides the criteria—like security, availability, and confidentiality—but you get to design and implement the specific controls that make sense for your unique tech stack and business operations.
This adaptability is exactly why it’s so valuable for everyone from SaaS platforms to data centers.
The whole point of a SOC 2 report is to show your stakeholders that you don’t just talk about security—you live it. It’s a powerful signal that your organization has moved beyond verbal promises to provide independently verified proof of sound security practices.
A huge part of being ready for an audit—and maintaining that readiness—is having solid document management best practices in place. This isn’t just about passing the audit; it’s about building a security culture that lasts.
The Growing Demand for SOC 2
The need for SOC 2 is exploding. It’s a clear reflection of a major market shift where security has become a primary factor in purchasing decisions.
The global market for SOC Reporting Services is on a steep climb, projected to grow from USD 5,392 million to USD 10,470 million by 2030. This growth is fueled by relentless cyber threats and increasing regulatory pressure. Right now, North America is leading the charge, holding a dominant 46.84% market share.
This trend tells a simple story: SOC 2 is no longer a “nice-to-have” badge. It’s rapidly becoming a fundamental requirement for doing business. It’s a serious investment in your company’s operational maturity and market credibility—one that pays off long after the audit is complete.
Navigating the Five Trust Service Criteria

At the very heart of any SOC 2 audit are the five Trust Services Criteria (TSCs). Think of them as the pillars holding up your entire security posture. Your auditor will evaluate your company’s systems and controls against a specific set of these criteria—the ones you choose based on your services and the promises you make to your customers.
Getting a handle on these five criteria is the first real step in scoping your audit. It helps you focus your compliance efforts on what actually matters to your business and your clients.
Let’s break them down. Imagine your company’s data environment is a secure digital castle.
The Foundation: Security
The Security criterion is the one non-negotiable part of every SOC 2. It’s often called the “Common Criteria” because it’s the bedrock for all the others. This principle is all about whether your system is protected against unauthorized access, both physical and logical.
In our castle analogy, Security is the castle itself—the high walls, the strong gates, and the vigilant guards. This covers everything from your access control policies and firewalls to intrusion detection. If the walls aren’t secure, nothing else inside can be.
The Four Optional Criteria
While Security is mandatory, you select from the other four criteria based on your business operations and what you’ve committed to your customers. This is one of the best parts of SOC 2—it’s flexible.
-
Availability: Does your service stay up and running as promised? In our analogy, are your castle gates open for business during the hours you’ve advertised? This involves disaster recovery planning, network performance monitoring, and incident response procedures to minimize downtime. If you have an SLA with a 99.9% uptime promise, you need this.
-
Processing Integrity: This one’s about your system doing exactly what it’s supposed to do—completely, accurately, and on time. If your castle operates a mint, does it produce the right number of coins, without errors? This is absolutely critical for financial platforms or any e-commerce transaction system.
-
Confidentiality: This applies to sensitive information that requires special protection. Think of this as the castle’s treasure room, only accessible to a few people with specific keys. It covers controls like data encryption and strict access restrictions for things like financial reports or intellectual property.
-
Privacy: While it sounds a lot like Confidentiality, Privacy is specifically about Personally Identifiable Information (PII). It looks at how you collect, use, retain, and dispose of personal data, making sure it aligns with your privacy notice. This is the castle’s policy for protecting the personal info of its citizens and visitors.
A key part of both Confidentiality and Privacy is ensuring data doesn’t stick around when it’s no longer needed. For any C-suite leader, managing end-of-life assets with compliant data destruction is a non-negotiable control.
Choosing Your Scope Strategically
Deciding which criteria to include in your audit is a business decision, not just a compliance one. You don’t need all five unless they’re all relevant. Over-scoping your audit leads to wasted time and money, but under-scoping gives you a report that might not satisfy your customers.
The goal is simple: align your SOC 2 report with your customer commitments. If you promise high availability in your contracts, you have to include the Availability criterion. If you handle sensitive financial data, Confidentiality is a must.
For FinTechs and fast-growing startups, getting this right with a Type II report can lead to some serious benefits, like 60% fine reductions and much faster sales cycles.
Your choice of TSCs defines the entire scope of your compliance journey. For a deeper look at how auditors apply these principles, check out our guide on the SOC 2 Trust Services Criteria. By carefully selecting the right criteria, you build a SOC 2 report that isn’t just a compliance checkbox—it’s a tool for building trust and closing deals.
Choosing Your Path: SOC 2 Type 1 vs. Type 2 Reports
Once you’ve nailed down your scope with the Trust Services Criteria, you’ll hit your next big fork in the road: choosing between a SOC 2 Type 1 and a Type 2 report. This isn’t just some technical checkbox; it’s a strategic call that will directly affect your sales cycle, customer trust, and your entire compliance roadmap.
Here’s a simple way to think about it: a Type 1 report is like an architect’s blueprint. An auditor shows up, inspects your security plans and controls on a single day, and confirms that—on paper—everything looks like it’s designed correctly. It’s a snapshot in time.
A Type 2 report, on the other hand, is like a year-long structural stress test of the finished building. The auditor isn’t just looking at the blueprints. They are actively monitoring and testing your controls over a period—usually six to twelve months—to prove they actually work day in and day out.
SOC 2 Type 1: The Point-in-Time Snapshot
A Type 1 report is all about the design of your controls at a specific moment. It answers one key question: “Are your security controls designed properly right now?”
This makes it a fantastic starting point for companies just dipping their toes into SOC 2.
It’s often used as a strategic stepping stone. We see tons of companies start with a Type 1 to get a baseline on the board and satisfy an urgent request from a big prospect. Because it doesn’t need a long observation period, a Type 1 audit can be wrapped up fast—often within a few weeks to a couple of months.
That speed can be a lifesaver when a high-value deal is on the line. It shows the customer you’re serious about security, even if you don’t have months of operational history to show for it yet.
SOC 2 Type 2: The Gold Standard of Assurance
While a Type 1 is useful, let’s be clear: the Type 2 report is what most enterprise customers and mature companies really want to see. It gives them a much higher level of assurance because it proves your controls have been operating effectively over time.
This report answers a much more powerful question: “Have your security controls been working consistently for the last year?” That sustained proof is invaluable. It shows you’ve got operational maturity and that your security isn’t just for show—it’s baked into your daily operations. The audit period for a Type 2 report typically covers 6 to 12 months.
A Type 2 report is the ultimate trust signal. It tells prospective customers that your commitment to security isn’t a one-time event, but a continuous, verified practice. It moves the conversation from “Are you secure?” to “We can prove we’ve been secure all year.”
Deciding between the two really comes down to your immediate business needs and where you’re headed long-term. To help you weigh the pros and cons for your specific situation, check out our detailed comparison of SOC 2 Type 2 vs Type 1 reports.
A Side-by-Side Comparison
Let’s break down the key differences to help you map out your compliance roadmap, whether you’re starting from scratch or aiming for the highest level of assurance.
Comparing SOC 2 Type 1 and Type 2 Reports
This table cuts right to the chase, showing you exactly where each report type shines and what it requires from your team.
| Attribute | SOC 2 Type 1 | SOC 2 Type 2 |
|---|---|---|
| Purpose | Evaluates the design of your security controls. | Evaluates the design and operating effectiveness of your controls. |
| Timeline | Assesses controls at a single point in time. | Assesses controls over a period of time (e.g., 6-12 months). |
| Speed | Faster to obtain, often completed in 1-3 months. | Slower to obtain, requiring the full observation period. |
| Effort | Lower initial effort and evidence collection. | Higher effort due to ongoing monitoring and evidence gathering. |
| Customer View | Good for initial assurance or urgent sales needs. | Considered the gold standard for long-term trust and enterprise deals. |
For many companies, the ideal path involves both. They kick things off with a Type 1 to get a report in hand quickly and unblock sales conversations, then immediately start the clock on their observation period for a Type 2. This builds on their initial foundation and proves they’re committed to ongoing operational excellence.
Your SOC 2 Roadmap: Timelines and Costs
So, you’re starting the SOC 2 journey. Let’s talk about what this is actually going to cost and how long it will take. This isn’t some black box of open-ended expenses; it’s a project with a predictable path. Once you understand the phases, the whole process feels a lot less daunting and a lot more like a manageable roadmap.
The entire path to SOC 2 compliance breaks down into three core stages: Readiness & Scoping, Remediation, and the actual Audit. Each one has its own timeline and price tag. We’ll walk through each so you can budget properly and set clear expectations.
Phase 1: Readiness and Scoping
This is where you lay the foundation. Think of a readiness assessment as a “pre-audit.” You bring in a consultant or your chosen audit firm to find all the gaps between what you’re doing now and what SOC 2 demands. It’s an absolutely critical step that saves you from expensive surprises down the road.
- Typical Timeline: 2 to 8 weeks
- Estimated Cost: $10,000 – $25,000
During this phase, you also lock down the audit’s scope—which Trust Services Criteria you’ll include and which of your systems need to be audited. A little investment here pays off big time by making the real audit much, much smoother.
Phase 2: Remediation
After the readiness assessment shows you where the holes are, it’s time to fix them. This is the “get your hands dirty” phase where your team implements new controls, writes and updates policies, and starts gathering the evidence to prove you’re doing what you say you’re doing.
The timeline and cost for remediation are the most unpredictable parts of the whole process. It really depends on what the assessment turns up.
If your security posture is already strong, you might knock this out in a few weeks. But if you’re a startup building everything from the ground up, expect to spend several months here. This is also the stage where you might decide to invest in compliance automation software or other security tools to make life easier.
Phase 3: The Formal Audit
Okay, your controls are in place and you’ve got the evidence to back them up. Now it’s time for the main event. The auditor digs in, reviewing your system description, testing your controls, and ultimately writing the final report. The timeline and costs here look very different for a Type 1 versus a Type 2 report.
This visual lays out the two distinct paths for a Type 1 (a snapshot of your controls’ design) and a Type 2 (a test of their effectiveness over time).
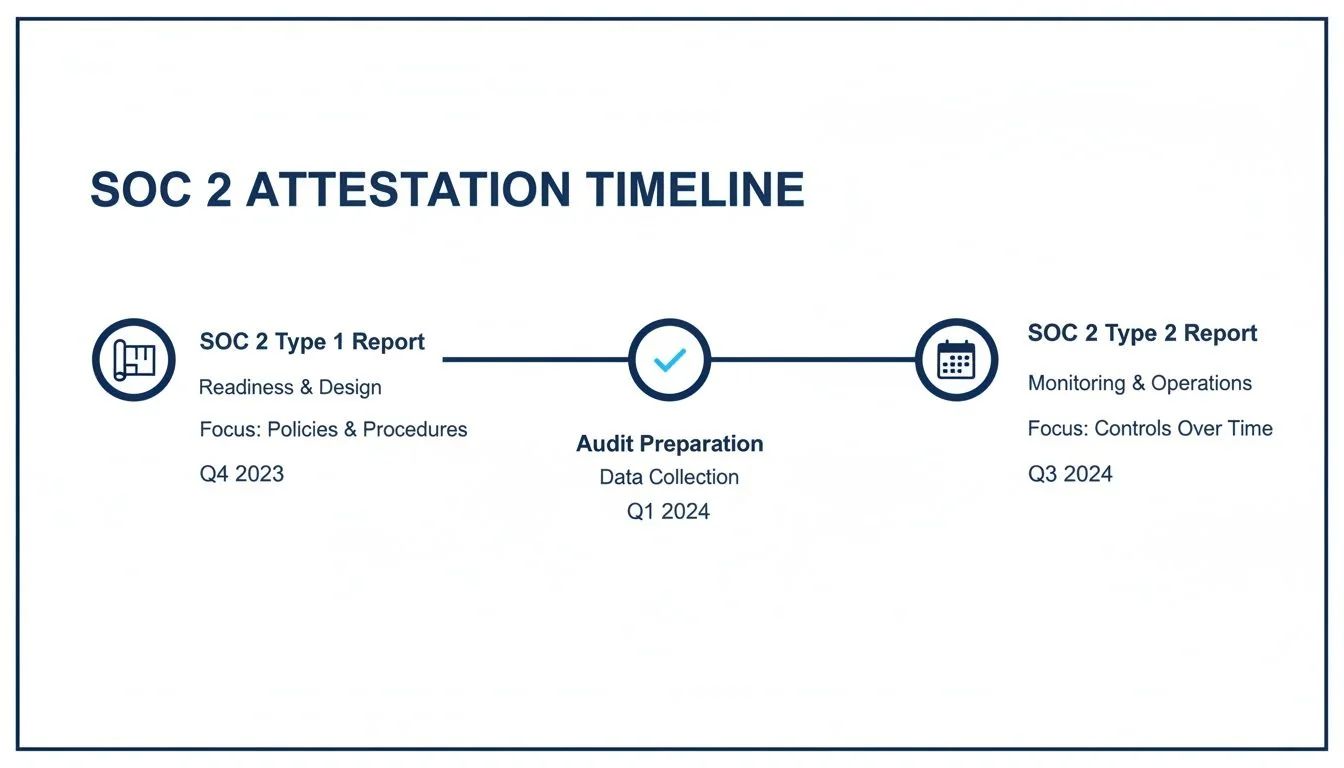
The key thing to notice is that while a Type 1 is a much faster win, a Type 2 report requires the auditor to watch your controls work over a sustained period, making it a much longer commitment.
- SOC 2 Type 1 Audit: This will typically set you back $15,000 - $30,000 and takes about 4 to 8 weeks to wrap up.
- SOC 2 Type 2 Audit: You’re usually looking at a range of $25,000 - $60,000+. This involves a 6 to 12-month observation period, followed by another 4 to 6 weeks for the auditor to do their fieldwork and write the report.
What Drives Your Final SOC 2 Cost?
That final price tag isn’t just a number pulled out of thin air. Several key factors determine the cost of your SOC 2 audit, and you need to understand them to compare quotes from different auditors. For a really deep dive on this, check out our guide on how much a SOC 2 audit costs.
Here are the main drivers:
- Company Size: More employees and more systems mean more things for an auditor to test. Simple as that.
- System Complexity: Auditing a complex, multi-cloud environment is going to cost more than a straightforward SaaS app.
- Audit Scope: Every Trust Services Criterion you add to the audit increases the workload and, consequently, the price.
- Audit Firm: There’s a big difference in fees between a boutique cybersecurity firm and one of the “Big Four” accounting giants.
This financial commitment is a big reason why you see a company’s funding stage often correlate with its SOC 2 status. Research from Venn shows that only about 7% of pre-seed and seed-stage startups have a SOC 2 report. That number jumps to 45% for companies with over $100 million in funding. It just goes to show how much of a resource barrier this can be for early-stage companies, making smart budgeting and planning that much more important.
How to Choose the Right SOC 2 Audit Partner
Choosing a SOC 2 auditor is one of the most important decisions you’ll make. This isn’t just hiring an inspector; it’s about finding a partner who can guide you through a messy, high-stakes process.
The right firm can make the audit a genuinely valuable exercise that actually strengthens your security. The wrong one can lead to months of delays, endless confusion, and a report that doesn’t even help you close deals.
So many companies make the classic mistake of picking an auditor based on price alone. And while cost definitely matters, a cheap audit from a firm that doesn’t know what they’re doing will cost you far more in wasted time and lost deals. A great auditor is both a technical expert and a strategic guide.
Look Beyond the Brand Name
When you start looking, you’ll see everyone from the massive “Big Four” accounting firms to tiny boutique auditors. It’s tempting to think a big name guarantees quality, but that’s rarely the case. What matters is finding a firm with the right experience for your company.
Focus on three things:
- Industry Experience: Have they audited SaaS companies like yours before? An auditor who gets the SaaS model won’t waste your time with irrelevant questions designed for a manufacturing plant. They’ll know the common pitfalls and best practices for your world.
- Technical Expertise: Your auditor has to understand your tech stack. If you’re a cloud-native shop running on AWS or Azure, you need a firm that lives and breathes cloud security, not one still thinking about on-premise servers.
- Communication and Support: How do they actually operate? Will you have a dedicated person to call, or are you just another ticket in a queue? A good partner is easy to get ahold of, communicates clearly, and is ready to jump on a call to answer questions.
Key Questions to Ask Potential Auditors
Those first few calls with potential auditors are your chance to really vet them. Don’t be afraid to dig in with tough questions that go beyond their sales pitch. This is your shot to see how they work and what kind of support you’ll actually get.
Walk into these meetings with a prepared list.
Your auditor should be a partner who helps you tell your security story, not an adversary trying to find fault. You’re looking for a firm that vibes with your company culture and genuinely wants you to succeed.
Here are the non-negotiable questions you should ask every single firm:
- What’s your experience with companies our size and in our industry? Push for specific, anonymized examples of clients similar to you. This proves they understand your business context and won’t just slap a generic template on your audit.
- How familiar is your team with our tech stack (e.g., AWS, GCP, Azure)? This is a deal-breaker. An auditor who doesn’t understand cloud infrastructure is going to cause unnecessary friction and massive delays.
- What does your evidence collection process look like? Do they use a modern portal for uploading everything, or are you going to be stuck in a nightmare of emailing spreadsheets back and forth? A clean process can save your team dozens, if not hundreds, of hours.
- Who will be our day-to-day contact, and what’s their background? You need to know if you’ll be working with a seasoned senior auditor or a junior associate on their first gig. The experience of your direct contact dramatically impacts your entire audit experience.
- What level of support can we expect during the observation period? Get specific about their policy on questions. Are they available for quick calls and Slack messages, or is every interaction a formal, ticketed request? Setting this expectation upfront is critical.
By focusing on these practical things—real-world experience, tech-savviness, and actual support—you can cut through the marketing fluff and find a real partner. This single choice will define your whole SOC 2 experience, making sure you not only get a clean report but also come out the other side with a stronger security posture.
Frequently Asked Questions About SOC 2 Compliance
The road to SOC 2 is paved with questions. Getting straight answers is the difference between a smooth audit and a painful, expensive detour. Here are the most common questions we hear from companies just starting out.
How Long Is a SOC 2 Report Valid?
Think of a SOC 2 report as having a shelf life of about 12 months. It’s not a one-and-done certificate you hang on the wall; it’s a snapshot of how your security controls performed over a specific period.
To keep trust high with enterprise customers and partners, you’ll need to renew it annually. This continuous cycle proves your security isn’t just a point-in-time project—it’s an ongoing commitment.
Is It Possible to Fail a SOC 2 Audit?
This is one of the biggest misconceptions out there. You don’t technically “pass” or “fail” a SOC 2 audit. Instead, the CPA firm issues a professional opinion on your controls.
The gold standard is an unqualified opinion. This is the clean bill of health you’re aiming for, meaning the auditor found no significant issues with how your controls are designed or operating.
Other outcomes are less ideal:
- Qualified Opinion: The auditor found one or more exceptions, but the rest of your security program is solid. It’s not a deal-breaker, but it raises questions.
- Adverse Opinion: This is the one you want to avoid. It means the auditor found serious, widespread problems in your control environment.
- Disclaimer of Opinion: The auditor couldn’t get enough evidence to form an opinion at all, which is a major red flag for any customer.
This is exactly why a readiness assessment is so critical. It helps you find and fix the gaps before the auditor does, setting you up for that clean, unqualified report.
What Is the Difference Between SOC 2 and ISO 27001?
While they’re both top-tier security standards, they solve different problems. SOC 2 is an attestation report that’s wildly popular in North America. It’s flexible, allowing you to build controls around the AICPA’s Trust Service Criteria that are relevant to your specific services.
ISO 27001, on the other hand, is a globally recognized certification for your entire Information Security Management System (ISMS). It’s much more prescriptive, demanding you follow a specific, structured framework for managing security across the whole organization.
In short, SOC 2 proves your controls for a specific system are working. ISO 27001 certifies your entire company’s program for managing information security. Many global companies end up getting both.
Do We Really Need a Readiness Assessment?
While it’s not technically required by the AICPA, skipping a readiness assessment is probably the single biggest mistake you can make on your first audit. Think of it as a dress rehearsal before opening night.
This is where you identify control gaps, missing policies, and evidence collection problems before the official audit clock starts ticking. Investing a little time and money here saves a massive amount of stress and rework later, dramatically boosting your chances of a smooth audit. It turns a mountain of unknowns into a predictable, manageable project.
Finding the right audit partner is the most critical step in your SOC 2 journey. At SOC2Auditors, we replace endless sales calls and confusing quotes with a data-driven matching platform. Compare 90+ verified firms on price, timeline, and industry expertise to find the perfect fit for your company in minutes. Get your free, tailored auditor matches at https://soc2auditors.org.