The SOC 2 common criteria are a set of 17 foundational security principles established by the American Institute of Certified Public Accountants (AICPA). These criteria, derived from the COSO framework, form the mandatory baseline for the Security Trust Services Criterion, which is a required component of every SOC 2 examination. Organizations must design, implement, and operate effective controls to meet these 17 criteria before they can undergo a SOC 2 audit, regardless of which additional Trust Services Criteria (Availability, Processing Integrity, Confidentiality, or Privacy) are included in the scope.
These criteria were developed by the American Institute of Certified Public Accountants (AICPA) and apply universally, no matter what your final report covers.
Understanding The Core Of Every SOC 2 Audit
The common criteria are not a simple compliance checklist; they represent the core principles of a well-governed and secure organization. They are based on the Committee of Sponsoring Organizations of the Treadway Commission (COSO) framework, an internationally recognized standard for internal control, governance, and risk management. For someone pursuing SOC 2, this matters because auditors use this framework to assess whether security is integrated into your corporate culture and processes, rather than being an afterthought.
An auditor will test your controls against these criteria to verify their design and operating effectiveness. If you are pursuing a SOC 2 report, meeting the common criteria is non-negotiable. They are the foundation upon which the entire audit is built. Without demonstrating adherence to these baseline requirements, your organization cannot achieve a clean SOC 2 report.
The Five Categories of Common Criteria
The 17 criteria are organized into five categories that directly map to the COSO framework. Approaching them within these groups helps structure your compliance efforts and demonstrates a mature, organized approach to security for your auditor.
Here’s the breakdown:
- CC1 Control Environment: This category assesses the organization’s commitment to integrity and ethical values, often referred to as the “tone at the top.” An auditor will look for evidence of board oversight, a commitment to attracting and retaining competent personnel, and structures for accountability.
- CC2 Communication and Information: This focuses on the flow of information required to support the functioning of internal control. For SOC 2, this means ensuring relevant, quality information about control objectives and responsibilities is generated and communicated effectively.
- CC3 Risk Assessment: This requires a formal process for identifying, analyzing, and responding to risks that threaten the achievement of the entity’s objectives. An auditor will expect to see a documented risk assessment methodology and a regularly updated risk register.
- CC4 Monitoring Activities: This category covers how you evaluate whether your controls are present and functioning. Auditors will test your ongoing monitoring activities, such as internal audits or vulnerability scans, to verify that controls are effective over time.
- CC5-CC9 Control Activities: This is the largest group, detailing the specific actions, policies, and procedures established to mitigate risks identified in CC3. These are the tangible controls an auditor will spend significant time testing.
Failing to meet even a single common criterion can lead to a qualified opinion or an adverse finding in your SOC 2 report. This compromises the entire purpose of the audit, which is to build trust with enterprise customers.
Mastering the common criteria is the most critical step toward SOC 2 audit readiness. It is the mechanism by which you prove to auditors and customers that your security program is built on a mature, recognized foundation. Without satisfying this baseline, passing a SOC 2 audit is impossible, making it the absolute centerpiece of your preparation.
Translating Common Criteria Into Actionable Controls
The SOC 2 common criteria are the mandatory, foundational requirements for every SOC 2 audit, focusing on governance, risk management, and security. To pass an audit, an organization must translate these abstract principles into specific, implemented controls and provide verifiable evidence that these controls are operating effectively. This process involves creating policies, deploying technology, and establishing procedures that directly address the objectives of the 17 criteria within the five core COSO categories.
This diagram shows how those five components stack up.
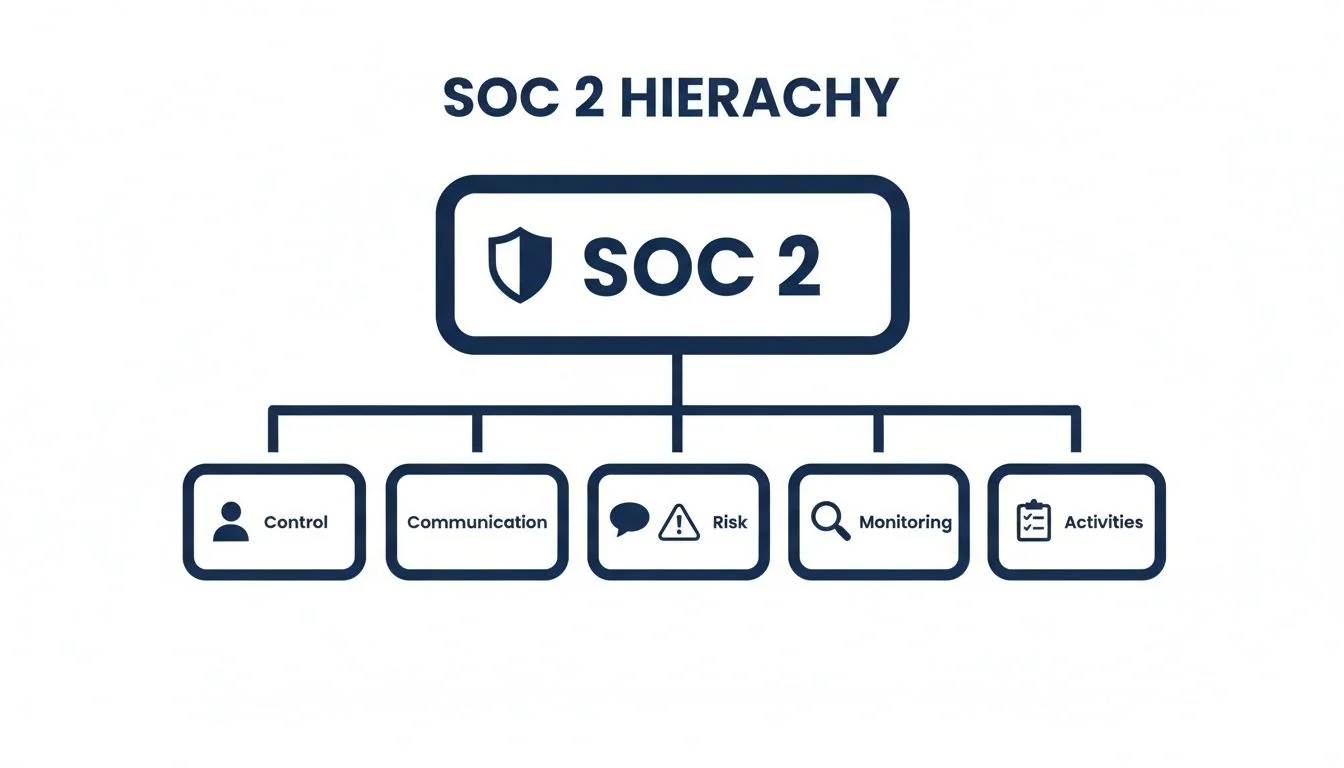
This structure is hierarchical. For someone pursuing SOC 2, this matters because it shows that effective control activities (CC5-CC9) are only possible when built upon a solid foundation of a sound control environment, clear communication, a formal risk assessment process, and continuous monitoring.
The Five COSO Categories Explained for SOC 2
Here’s a breakdown of what auditors require within each of the five common criteria categories from a SOC 2 compliance perspective.
CC1: The Control Environment
This category assesses the “tone at the top.” An auditor must see evidence that leadership is committed to integrity and ethical values. For someone pursuing SOC 2, this is critical because a weak control environment is a significant red flag for an auditor, suggesting that security controls may be circumvented because leadership does not enforce them. To satisfy CC1, you must provide tangible proof of leadership’s engagement in governance and oversight.
- AICPA Requirement (CC1.1): “The entity demonstrates a commitment to integrity and ethical values.”
- Auditor Evidence Request: “Provide the Board of Directors’ meeting minutes from the last quarter where information security risk was formally discussed.”
- Actionable Guidance: Ensure your board meeting minutes explicitly document the review of risk assessments, discussions of security incidents, or approval of the annual security budget. This serves as direct evidence of oversight.
- AICPA Requirement (CC1.2): “The board of directors demonstrates independence from management and exercises oversight of the development and performance of internal control.”
- Auditor Evidence Request: “Show me the employee handbook or Code of Conduct, along with proof that every employee has acknowledged it.”
- Actionable Guidance: Use an HRIS or a document management tool to collect digital signatures from all personnel. This creates a clean, auditable log demonstrating company-wide acceptance of ethical and security standards.
CC2: Communication and Information
These criteria focus on how an organization creates, manages, and disseminates information to support the functioning of its internal controls. For someone pursuing SOC 2, this is vital because controls are ineffective if the relevant personnel are unaware of them or do not understand their responsibilities. An auditor needs to see a structured flow of information regarding policies, procedures, and responsibilities throughout the organization.
An auditor will look for evidence that you not only wrote policies but also effectively communicated them to the right people. A policy sitting unread on a server somewhere provides zero security value and fails this test every time.
Here’s how you generate audit-ready evidence:
- Documented Policies (CC2.1): Establish a centralized repository (e.g., a wiki or document management system) for all security policies. Implement version control and an annual review schedule to demonstrate that policies are current and actively managed.
- Training Logs (CC2.2): Conduct security awareness training for all new hires and provide annual refreshers. Your auditor will require completion reports from your training platform as evidence of participation.
- Incident Communication (CC2.3): Document your incident response communication plan. Be prepared to show records from a dedicated communication channel (like a Slack channel) or ticketing system used during a past or simulated event to prove effective internal communication.
CC3: Risk Assessment
The Risk Assessment criteria mandate a formal process for identifying, analyzing, and responding to risks. This cannot be an informal brainstorming session; it must be a structured, documented methodology that an auditor can inspect and validate. For someone pursuing SOC 2, this matters because a formal risk assessment proves that your security controls are not arbitrary. It demonstrates they were specifically designed to mitigate the unique threats your business faces, reflecting a mature and proactive approach to security.
Your primary evidence will be a risk register, which must list all identified risks and include:
- Risk Description (CC3.1): A clear explanation of the threat (e.g., “Unauthorized access to production database due to stolen developer credentials”).
- Impact & Likelihood Score (CC3.2): A rating for each risk (e.g., High Impact, Medium Likelihood) based on your documented risk scoring methodology.
- Mitigating Controls (CC3.4): The specific controls implemented to reduce the risk (e.g., “MFA on all production systems,” “Quarterly access reviews”).
- Risk Owner: The individual or team assigned responsibility for managing the risk.
CC4: Monitoring Activities
These criteria require you to prove that your controls are operating effectively over time. It is not sufficient to simply implement a control; you must continuously monitor it to ensure its effectiveness and identify deficiencies. For someone pursuing a SOC 2 Type 2 audit, this is especially important, as the audit covers a period of time (typically 6-12 months). Auditors need to see evidence that controls operated consistently throughout the entire audit window.
Examples of robust monitoring evidence include:
- Internal Audit Reports (CC4.1): If you have an internal audit function, their reports on control effectiveness are primary evidence.
- Vulnerability Scan Reviews (CC4.2): Provide reports from your vulnerability scanner (e.g., Tenable, Qualys) and evidence that findings were reviewed and remediated, such as tickets in a system like Jira created to track the remediation of high-risk vulnerabilities.
- Log Review Dashboards: Show the auditor your SIEM dashboard or log management tool, demonstrating that security events are actively monitored and alerted on. To properly address the Processing Integrity criteria, it’s vital to implement robust data integrity best practices in your systems.
CC5 to CC9: Control Activities
Control Activities are the largest and most detailed group of criteria, representing the specific actions, policies, and procedures implemented to mitigate risk. This is where the principles from the other criteria are put into practice. For someone pursuing SOC 2, these criteria are the core of the audit because they cover the technical and process controls that directly protect customer data. Auditors will spend a significant portion of their time testing these controls. For a much deeper look, check out our guide on essential SOC 2 controls.
- CC6 (Logical & Physical Access): Evidence includes artifacts like quarterly logical access reviews where managers certify their direct reports’ system access. An auditor will sample these records to test the control’s operating effectiveness.
- CC7 (System Operations): Evidence here includes the documented incident response plan and post-mortem reports from any past security events, demonstrating a formal process to detect, respond to, and learn from incidents.
- CC8 (Change Management): An auditor will request a sample of change management tickets from your system (e.g., Jira, ServiceNow). These tickets must provide evidence of peer review, testing, and formal approval before code was deployed to a production environment.
To help you connect the dots, this table shows how each COSO category translates into a real-world control objective and the kind of evidence an auditor will ask for.
Mapping Common Criteria To Practical Controls And Evidence
| COSO Category (Common Criteria) | Control Objective Example | Auditor Evidence Request Example |
|---|---|---|
| CC1: Control Environment | Leadership demonstrates a commitment to integrity and ethical values. | Provide Board of Directors meeting minutes where security risk was reviewed. |
| CC2: Communication | Security policies and procedures are documented and communicated to all personnel. | Provide a link to the internal policy wiki and security awareness training completion reports. |
| CC3: Risk Assessment | The organization identifies and analyzes risks to the achievement of its objectives. | Provide the formal risk register, including risk scores and mitigation plans. |
| CC4: Monitoring Activities | The organization monitors control effectiveness and remediates deficiencies. | Provide vulnerability scan reports and the Jira tickets created to address high-risk findings. |
| CC5-9: Control Activities | Changes to production systems are authorized, tested, and approved before implementation. | Provide a sample of 25 change management tickets showing peer review and management approval. |
This table serves as a practical guide for the entire process, illustrating the path from abstract compliance requirements to concrete, auditable actions.
Scoping Your Audit With The Five Trust Services Criteria
The Trust Services Criteria (TSC) are the five categories used by auditors to evaluate the design and operating effectiveness of an organization’s controls in a SOC 2 audit. These criteria—Security, Availability, Processing Integrity, Confidentiality, and Privacy—are established by the AICPA. For someone pursuing SOC 2, understanding how to scope the audit with these criteria is a critical strategic decision.
While the Security criterion is mandatory for all SOC 2 audits, the other four are optional. The selection of additional criteria should be based on the services provided, commitments made to customers, and contractual requirements. Incorrectly scoping the audit can lead to unnecessary costs or a final report that fails to meet customer expectations.

This is not about achieving “maximum compliance” by including all five criteria. It’s about strategic alignment. Adding a criterion not relevant to your business wastes resources on unnecessary controls. Conversely, omitting a criterion that a key customer requires can render the entire audit report useless to them.
Security: The Mandatory Foundation
Every SOC 2 audit must include the Security criterion. This criterion addresses the protection of systems and information against unauthorized access, unauthorized disclosure, and damage. Why does this matter for someone pursuing SOC 2? The Security criterion, whose requirements are detailed in the common criteria, serves as the non-negotiable baseline. It demonstrates that fundamental safeguards like access controls, change management, and risk mitigation are in place. Without this foundation, any promises related to the other criteria would be unsubstantiated.
Availability: For Services That Must Not Fail
The Availability criterion is for organizations whose services must be accessible and usable as committed or agreed. This is relevant if uptime is a core component of your value proposition and is governed by strict Service Level Agreements (SLAs). Why does this matter for someone pursuing SOC 2? If your customers rely on your platform for their own business operations, you must provide assurance of its reliability. Auditors will examine controls related to performance monitoring, disaster recovery, and incident management to validate your availability claims.
To meet this criterion, you will need to provide evidence such as:
- Disaster Recovery Test Results: Verifiable proof that you have tested your DR plan and can meet your stated Recovery Time Objectives (RTOs).
- System Performance Monitoring: Dashboards and alerting configurations from monitoring tools demonstrating that system health and availability are tracked against SLA commitments.
- Incident Response Post-Mortems: Documentation from any downtime incidents detailing root cause, remediation actions, and preventive measures implemented.
Processing Integrity: For Accurate And Complete Data
Processing Integrity addresses whether a system processes data completely, validly, accurately, and in a timely manner. This is essential for services involving transactions or critical calculations, such as financial processing platforms, data analytics tools, or payroll services. Why does this matter for someone pursuing SOC 2? If your service modifies or calculates customer data, you must prove the output is reliable. Auditors will scrutinize controls that ensure data integrity throughout the processing lifecycle.
Key controls and evidence for this criterion include:
- Input Validation: System configurations that enforce rules to reject incomplete or improperly formatted data upon submission.
- Data Reconciliation Reports: Regularly generated reports that compare processed data against source data to identify and correct discrepancies.
- Quality Assurance (QA) Testing Records: Documentation showing that your QA team has specifically tested and verified processing accuracy as part of new software release cycles.
Confidentiality: For Protecting Sensitive Information
The Confidentiality criterion applies when you handle data designated as ‘confidential’ by agreement or policy. It focuses on the controls used to protect this specific information from unauthorized disclosure throughout its lifecycle. Why does this matter for someone pursuing SOC 2? If you store or process customers’ sensitive business information—such as intellectual property, strategic plans, or financial records—this criterion demonstrates you have targeted controls to protect data with strict access restrictions. You can learn more about how all five TSCs work together in our comprehensive guide to the SOC 2 Trust Services Criteria.
Auditors will require evidence such as:
- Data Encryption: Proof that confidential data is encrypted both in transit (e.g., TLS configurations) and at rest (e.g., database encryption).
- Access Control Lists (ACLs): System configurations demonstrating that access to confidential data is restricted to authorized individuals based on the principle of least privilege.
- Non-Disclosure Agreements (NDAs): Executed NDAs with employees and third-party vendors who may have access to confidential information.
Privacy: For Protecting Personal Information
The Privacy criterion is distinct from Confidentiality and focuses exclusively on the protection of Personally Identifiable Information (PII). It examines how an organization collects, uses, retains, discloses, and disposes of personal data in conformity with the commitments in its privacy notice. Why does this matter for someone pursuing SOC 2? If your service handles any PII from customers or their end-users (e.g., names, email addresses, health records), this criterion is crucial for demonstrating adherence to privacy commitments and regulatory requirements.
Controls for Privacy often include:
- Published Privacy Notice: A publicly accessible privacy policy that clearly describes how personal data is handled.
- Consent Management: A system for obtaining and tracking user consent for the collection and processing of their PII.
- Data Deletion Processes: A documented and tested process for securely deleting PII upon user request or when it is no longer required.
Selecting the correct Trust Services Criteria is a strategic business decision, not just a compliance task. Proper scoping prevents a costly, drawn-out audit while ensuring the final report meets the expectations of your most important customers and prospects.
Don’t Start SOC 2 From Scratch: How to Use Frameworks You Already Have
If your organization has previously undergone an ISO 27001 audit or aligned its security program with the NIST Cybersecurity Framework (CSF), you have a significant advantage in preparing for SOC 2. These existing frameworks are strategic assets, not just historical compliance artifacts. For someone pursuing SOC 2, this matters because leveraging prior compliance work can dramatically reduce the time and effort required for audit preparation.
The fundamental principles of information security—such as risk management, access control, and incident response—are universal across these frameworks. The evidence collected for a previous audit, such as policies, procedures, and configuration screenshots, can often be directly repurposed for SOC 2. Mapping existing controls to SOC 2 requirements is one of the most effective strategies for streamlining the audit process.
Mapping ISO 27001 to the SOC 2 Common Criteria
ISO 27001 is structurally similar to SOC 2, as both are risk-based frameworks focused on establishing a comprehensive information security management system (ISMS). Significant overlap exists between ISO 27001’s Annex A controls and the SOC 2 common criteria, particularly within the Control Activities sections (CC6-CC9).
For example, consider logical access controls, a critical area for any SOC 2 audit.
- SOC 2’s CC6.1 requires the implementation of logical access security measures to protect information assets.
- ISO 27001’s Annex A.5.15 (Access Control) focuses on managing user access rights throughout the user lifecycle.
The evidence required to satisfy both is identical: documented access control policies, records of periodic user access reviews, and logs showing timely de-provisioning of former employees. If this evidence was prepared for an ISO 27001 audit, it can be directly reused for SOC 2.
Repurposing evidence is the key to efficiency. For every overlapping control, you save dozens of hours that would otherwise be spent re-documenting processes and pulling new evidence samples for your SOC 2 auditor.
This overlap is consistent across multiple domains. Your risk assessment process from ISO 27001 (A.6.1.2) directly supports SOC 2’s CC3 series on risk management. Your incident management procedures (A.5.24) align perfectly with SOC 2’s CC7. Research shows that 58% of companies are now conducting four or more audits simultaneously, with ISO 27001 and SOC 2 consistently ranked as top priorities due to their interconnected nature. You can learn more about these compliance trends and statistics and how they’re shaping modern audit strategies.
The following table provides a high-level mapping of critical SOC 2 Common Criteria to their corresponding ISO 27001 Annex A control domains.
SOC 2 Common Criteria vs ISO 27001 Annex A Control Mapping
| SOC 2 Common Criterion (CC) | Corresponding ISO 27001 Annex A Domain | Example Overlapping Control |
|---|---|---|
| CC3: Risk Management | A.5.12: Information security in supplier relationships | Vendor risk assessments and third-party due diligence processes. |
| CC5: Control Activities | A.5.1: Policies for information security | Documented and approved information security policies. |
| CC6: Logical Access | A.5.15: Access control | User access reviews, role-based access control (RBAC), and MFA. |
| CC7: System Operations | A.8.16: Monitoring activities | System monitoring tools (e.g., SIEM) and vulnerability scanning. |
| CC8: Change Management | A.8.32: Change management | Documented change request, approval, and testing processes. |
| CC9: Risk Mitigation | A.5.34: Information security incident management | Incident response plans, runbooks, and post-mortem analyses. |
By using this mapping, you can quickly identify existing controls, determine which ones need modification, and focus your efforts on genuine gaps.
Connecting NIST CSF to SOC 2
While the NIST Cybersecurity Framework is not a certifiable standard, its structure provides an excellent model for organizing and presenting your SOC 2 controls. The CSF’s five core functions—Identify, Protect, Detect, Respond, and Recover—offer a logical narrative that demonstrates program maturity to an auditor. For someone pursuing SOC 2, this is important because it shows that your controls are not a random collection of activities but part of a cohesive, risk-informed security program.
The NIST CSF ‘Protect’ function, for instance, is defined as developing and implementing appropriate safeguards to ensure the delivery of critical services. This objective aligns directly with several key SOC 2 common criteria:
- CC6 (Logical and Physical Access Controls): Controls such as multi-factor authentication and role-based access are prime examples of the ‘Protect’ function.
- CC7 (System Operations): System monitoring and vulnerability management are fundamental activities for protecting information assets.
- CC8 (Change Management): A formal change management process prevents unauthorized modifications that could weaken security defenses.
By organizing your SOC 2 evidence according to the NIST CSF functions, you present a coherent story about your security program. This demonstrates to an auditor that your controls are part of a thoughtful, systematic approach to protecting customer data.
How To Choose The Right Auditor For Your Business
Selecting a SOC 2 auditor is a critical decision in the compliance process. The audit must be conducted by an independent Certified Public Accountant (CPA) firm, but the choice goes far beyond a simple procurement exercise. For someone pursuing SOC 2, this matters because the right audit partner must understand your technology stack, industry context, and business model to perform an effective and efficient audit. A well-suited auditor can provide valuable guidance, whereas a poor fit can result in a frustrating, costly, and inefficient process.
A great auditor offers clear direction while maintaining their professional independence, turning the audit into a valuable exercise that strengthens your security posture. A mismatched auditor often leads to scope creep, ambiguous evidence requests, and a painful process that feels punitive rather than productive.
Evaluating An Auditor’s Technical And Industry Expertise
Not all CPA firms possess the same level of technical proficiency. An auditor primarily experienced with traditional on-premise environments may not fully grasp the nuances of a cloud-native SaaS architecture. This knowledge gap can lead to irrelevant evidence requests and a fundamental misinterpretation of how your controls are implemented.
When vetting potential audit firms, ask targeted questions about their experience with your specific technology environment:
- Cloud Platforms: Have they audited organizations that are heavily reliant on AWS, Google Cloud, or Azure? Do they understand platform-native security services, or are they accustomed to traditional server log reviews?
- DevOps and CI/CD: Are they familiar with modern software development lifecycle practices? An auditor who understands CI/CD pipelines can assess your change management controls more effectively than one who expects manual, ticket-based approvals for every change.
- Industry Experience: Does the firm have a portfolio of clients in your vertical, such as FinTech or HealthTech? An auditor with relevant industry experience will already be familiar with the specific risks and regulatory pressures you face.
Assessing The Audit Process And Project Management
An auditor’s methodology is as important as their technical expertise. A disorganized audit process creates significant friction for your team, causing delays and unnecessary stress. In contrast, a well-managed audit functions like a structured project with clear milestones and expectations.
Key factors to evaluate include:
- Communication Style: Will you have a dedicated point of contact, or will you be routed through a generic support queue? What is their standard response time for inquiries?
- Evidence Management: Do they use a modern, secure portal for evidence submission, or will you be required to manage evidence via email and spreadsheets?
- Clarity of Requests: Ask for a sample evidence request list. Are the requests clear, specific, and actionable, or are they vague and open to interpretation?
The global SOC Reporting Services market was valued at USD 5,392 million and is projected to reach USD 10,470 million by 2030. Audit and Compliance Services constitute the largest segment at 44.99%, underscoring the critical role of this process for businesses. You can find more insights on the growth of the SOC reporting market.
The Importance Of Independence And Partnership
An auditor must maintain independence and objectivity as a core professional standard. However, this does not preclude them from being a supportive partner in the audit process. The best auditors balance these roles by offering guidance on how to meet the requirements of the SOC 2 common criteria without designing or implementing your controls for you. They can explain why a control is deficient and what the standard requires, but it remains your responsibility to design and implement the solution.
A great auditor will teach your team how to think about risk and controls, leaving your security posture stronger long after the audit is complete. A compliance-focused auditor will just check boxes, providing little long-term value.
During your evaluation calls, pay close attention to how they describe their role. Do they position themselves as strict examiners or as partners in a rigorous assessment? Their language will reveal their audit philosophy.
Building Your Audit Readiness Action Plan
A successful SOC 2 audit is the result of a deliberate, structured process, not a last-minute effort. The process begins with a thorough understanding of the SOC 2 common criteria and culminates in selecting a qualified audit partner. For someone pursuing SOC 2, this matters because a structured action plan transforms the abstract goal of “achieving compliance” into a manageable project with a clear path forward.
The journey progresses logically from high-level strategic decisions, such as audit scope, to the detailed, tactical work of remediating control gaps and gathering evidence.
By following a systematic approach, you ensure that when the audit commences, you have built a defensible security program supported by a comprehensive trail of evidence.
Your Five-Step Readiness Roadmap
To organize your compliance efforts, follow this proven five-step process. Each step builds upon the previous one, creating momentum and ensuring that no critical requirements are overlooked on the path to a clean SOC 2 report.
- Formally Scope Your Audit: Determine which Trust Services Criteria, beyond the mandatory Security criterion, are relevant to your business. This decision should be based on your service commitments, contractual obligations, and customer expectations. Correctly defining the scope prevents wasted effort and ensures the final report meets market needs.
- Perform a Detailed Gap Analysis: With a defined scope, conduct a rigorous assessment of your existing controls against the 17 Common Criteria and any additional selected criteria. This involves mapping your current practices to the AICPA requirements to identify all control gaps.
- Create a Remediation Plan: For each identified gap, create a specific, actionable remediation task. Assign a clear owner responsible for closing the gap and establish a realistic deadline. This plan serves as your project roadmap, converting audit findings into a concrete to-do list.
- Implement Controls and Gather Evidence: Systematically implement the controls outlined in your remediation plan. Critically, as each control is implemented, immediately collect the evidence required by an auditor (e.g., screenshots, policy documents, system logs, meeting minutes). This “collect as you go” approach streamlines the final evidence submission process.
- Engage a Qualified Auditor Early: Do not wait until you believe you are “ready” to begin discussions with auditors. Engage a firm early in the process to align on scope, methodology, and evidence expectations. An early partnership minimizes surprises and helps focus your remediation efforts on what is most important for the audit.
Mastering the Common Criteria isn’t just a technical exercise; it’s the fundamental requirement for proving a mature security posture to the enterprise clients you want to win. It is the language of trust in the B2B world.
A successful SOC 2 audit begins with a deep understanding and methodical implementation of these core principles. The process demands rigor, but the resulting benefits—accelerated sales cycles and enhanced customer trust—are significant. Ultimately, achieving a successful SOC 2 report is a direct result of thorough preparation, and a deep understanding of the common criteria is the cornerstone of effective SOC 2 audit readiness.
Finding the right auditor is a critical step in your SOC 2 journey. At SOC2Auditors, we replace the guesswork with data, providing a platform to compare 90+ firms on pricing, timelines, and verified client feedback. Get three tailored auditor matches in 24 hours and make your selection with confidence by visiting https://soc2auditors.org.